USG40 L2TP IPSEC VPN : PHASE 2 LOCAL POLICY MISMATCH
Options
Hi everyone,



I'm trying to set up an L2TP/IPSEC VPN on a USG40, the basic network config is as follow :
The VPN connection config is attached as images (screen caps).
It has been set up following another post found on this forum but it does not work.
I tried connecting using Android 10 client and Windows 10
 integrated client.
integrated client.
Can you help me ?
Thanks a lot,
Sebastien
EDIT
Attachment doesn't seem to work, here a are the links to screen caps:
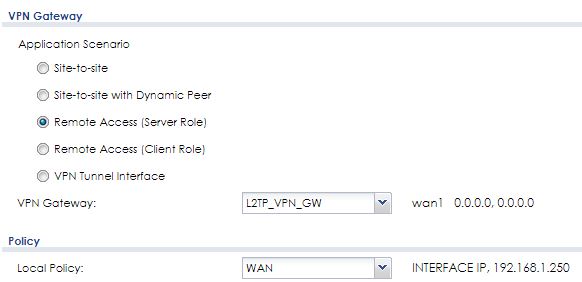
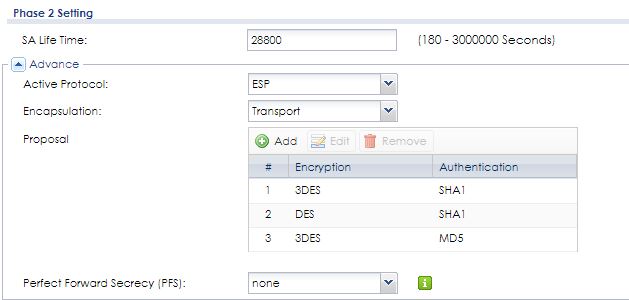



I'm trying to set up an L2TP/IPSEC VPN on a USG40, the basic network config is as follow :
- WAN connected to a VSDL router, fixed IP 192.168.1.250
- UDP ports 500, 1701 and 4500 redirected to 192.168.1.250
- All LAN ports in LAN1 zone subnet 10.0.0.0/24
- ZyWall IP 10.0.0.1
410 | 2020-05-28 21:18:15 | info | IKE | ISAKMP SA [L2TP_VPN_GW] is disconnected | 192.168.1.250:4500 |  109.143.170.251:4500 109.143.170.251:4500 | IKE_LOG |
411 | 2020-05-28 21:18:15 | info | IKE | Received delete notification |  109.143.170.251:4500 109.143.170.251:4500 | 192.168.1.250:4500 | IKE_LOG |
412 | 2020-05-28 21:18:15 | info | IKE | Recv:[HASH][DEL] |  109.143.170.251:4500 109.143.170.251:4500 | 192.168.1.250:4500 | IKE_LOG |
413 | 2020-05-28 21:18:15 | info | IKE | Send:[HASH][NOTIFY:NO_PROPOSAL_CHOSEN] | 192.168.1.250:4500 |  109.143.170.251:4500 109.143.170.251:4500 | IKE_LOG |
414 | 2020-05-28 21:18:15 | info | IKE | [SA] : No proposal chosen | 192.168.1.250:4500 |  109.143.170.251:4500 109.143.170.251:4500 | IKE_LOG |
415 | 2020-05-28 21:18:15 | info | IKE | [ID] : Tunnel [L2TP_VPN_CON] Phase 2 Local policy mismatch | 192.168.1.250:4500 |  109.143.170.251:4500 109.143.170.251:4500 | IKE_LOG |
416 | 2020-05-28 21:18:15 | info | IKE | Recv:[HASH][SA][NONCE][ID][ID][PRV][PRV] |  109.143.170.251:4500 109.143.170.251:4500 | 192.168.1.250:4500 | IKE_LOG |
417 | 2020-05-28 21:18:15 | info | IKE | Phase 1 IKE SA process done | 192.168.1.250:4500 |  109.143.170.251:4500 109.143.170.251:4500 | IKE_LOG |
The VPN connection config is attached as images (screen caps).
It has been set up following another post found on this forum but it does not work.
I tried connecting using Android 10 client and Windows 10

 integrated client.
integrated client.Can you help me ?
Thanks a lot,
Sebastien
EDIT
Attachment doesn't seem to work, here a are the links to screen caps:


0
Accepted Solution
-
Have you set related settings to zone IPSec_VPN? You then need a routing rule for incoming tunnel L2TPVPNWAN to SNAT and a firewall rule from IPSec_VPN to WAN.
5
All Replies
-
The USG40 is placed behind NAT.You should follow the guide to configure the wan IP of VSDL router as "Local Policy".0
-
Thanks for your reply.
Yes it is behind a NAT and your article is interesting.
If I read it correctly the local policy for phase 2 should be the WAN public IP, not the USG40 WAN IP.
This is a problem for my scenario because the public IP is dynamic. To bypass this, I create a FQDN object pointing to my VSDL router but I can't select that type of object for phase 2 local policy (not shown in the list).
Is there a way to do the same thing with a dynamic publicv address you think ?
Regards,
Sebastien0 -
Yes it is ! I found the solution : I set up the local policy to an IP object, type HOST, value 0.0.0.0.
My L2TP is now working for local network, but no access to Internet when VPN conencted despite the security rules allow traffic between the IP Sec zone and any other zones.
So a ping to 10.0.0.0/24 subnet is OK but not to 8.8.8.8.
Please note that I had to configure the IP pool to the subnet 10.0.2.0/24 but as ping works to 10.0.0.1 I suppose it is not a routing issue.
Nothing in the logs saying that ping from 10.0.2.1 to 8.8.8.8 packets are blocked.
Thanks for your help.
0 -
Have you set related settings to zone IPSec_VPN? You then need a routing rule for incoming tunnel L2TPVPNWAN to SNAT and a firewall rule from IPSec_VPN to WAN.
5 -
Thank you PeterUK that was the answer, I have created a Policy Route from L2TP Zone to SNAT on the outgoing interface and bingo Internet is there. Works perfectly for my smartphone beside SSL VPN.

0 -
Hello Sébastien, I have very similar problem right now.
Could you please send me your configuration, because I am stuck in the situation, that the IPsec tunnel is established, but then the client (Windows 7) starts waiting for some response and after 20-30 seconds ends up with error 809 (remote server does not respond).
If you could help me anyhow I would be very greatful.0 -
Hello Lukas, are you running the IKE and AuthIP IPsec Keying Modules service on Windows? The service must be enabled and running.
0 -
Hello Lukas, what do the logs say on the USG ? This is where you should begin your investigation because problems could look the same but be very different. Could you post the logs when you try to connect the tunnel ?
There is also a trick to allow Windows client to connect to an IPSec tunnel behind a NAT-T, please look at https://support.microsoft.com/en-us/help/926179/how-to-configure-an-l2tp-ipsec-server-behind-a-nat-t-device-in-windows for more information.
Regards,
Sebastien0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Freshman Member
Freshman Member


 Guru Member
Guru Member


 Master Member
Master Member





