FLEX 100H firewall zone bug
 Freshman Member
Freshman Member



We ran into some odd behavior that appears to be a bug on a FLEX 100H running latest 1.32 firmware.
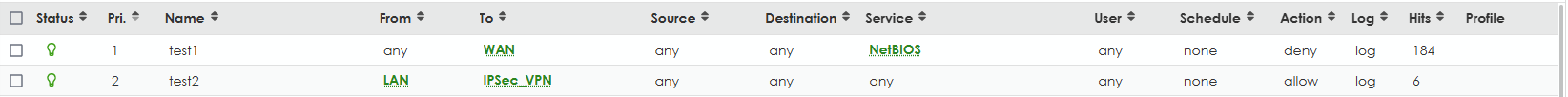
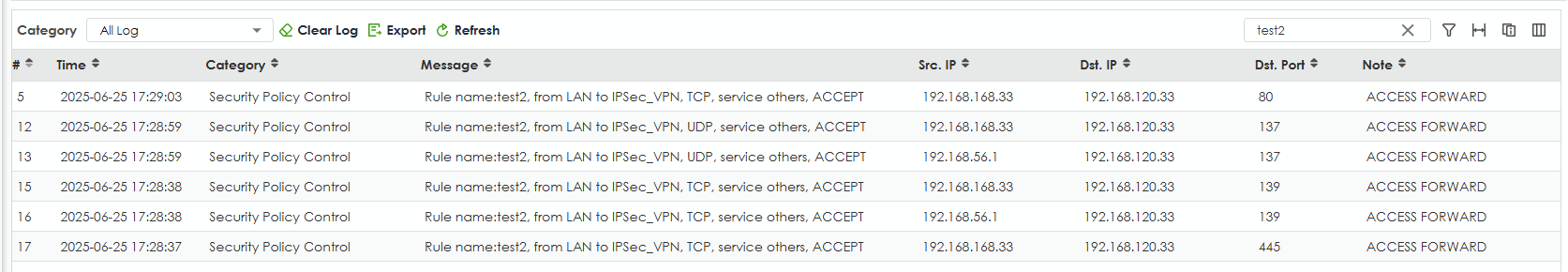
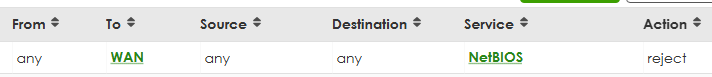
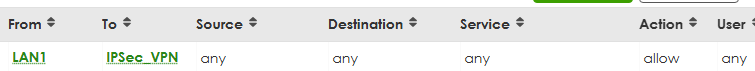
We have a firewall rule which blocks NetBIOS packets from ANY-to-WAN, and another rule which allows all packets from LAN-to-IPSec. For some reason, the ANY-to-WAN rule is blocking packets that are supposed to be sent over the VPN.
We can work around this issue if we reverse the order of these rules so the IPSec rule is above the ANY-to-WAN rule.
Why is the ANY-to-WAN rule blocking destination IPs which should be in the IPSec zone?
See screenshots below.
All Replies
-
Have seem this too
0 -
Hi @p4_greg
Could you enable the Zyxel support access for this site on Nebula and share an account for us to check this issue? I will send you a private message for the account info.
I did a local test that my policy rules are same as yours, but didn't see this issue.
Zyxel Melen0 -
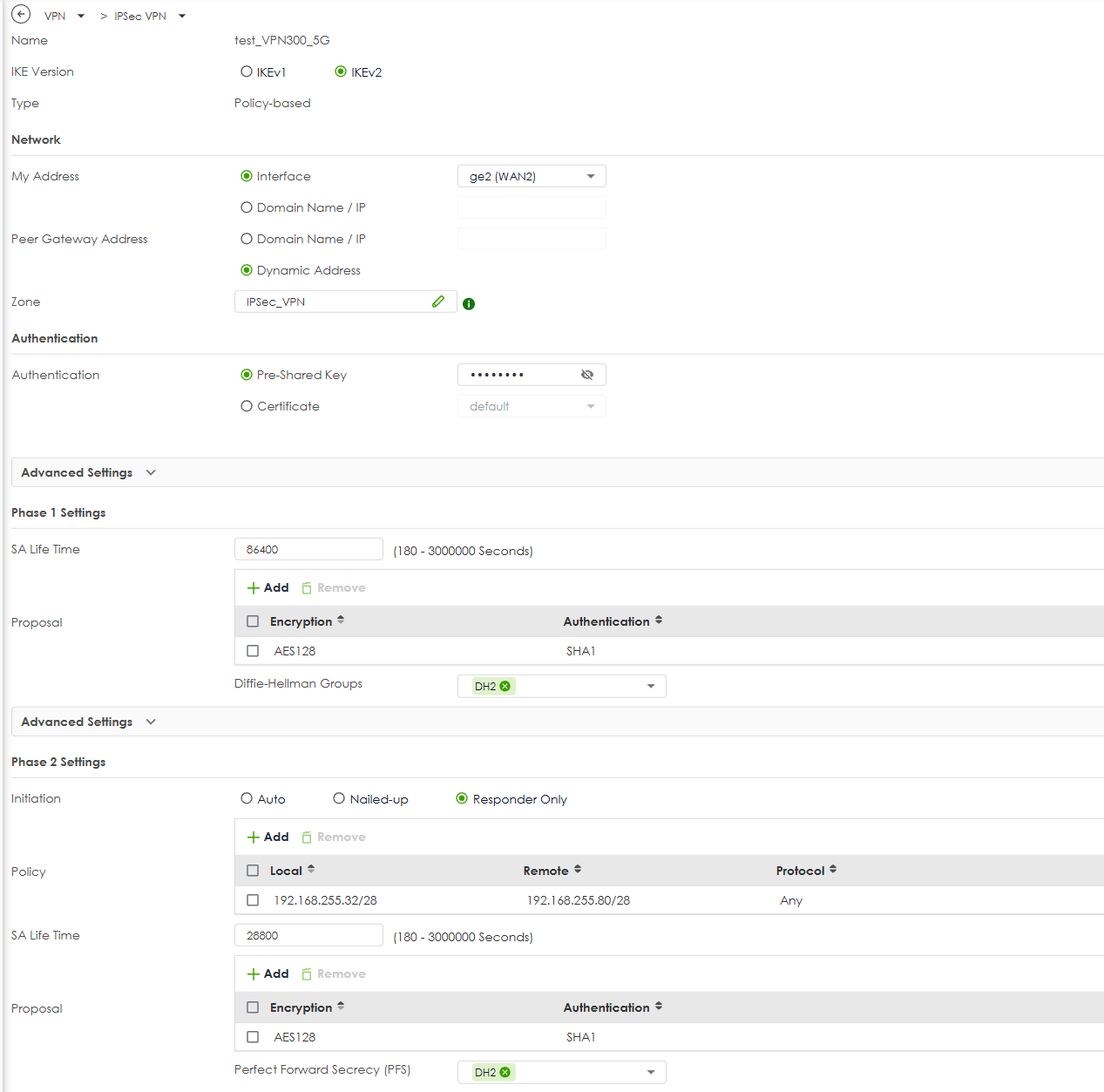
@Zyxel_Melen Is your test using Policy-based IPSec VPN or Route-based(VTI)?
We have seen this same issue on 2 different networks/routers using FLEX 100H on both sides of a Policy-based VPN.
These routers/networks are in production at our client's locations, so if you truly cannot re-create this issue in your lab I will likely have to set up some test units for you to look at.
0 -
Can confirm this is still a issue
tested on two different subnets with both being /28
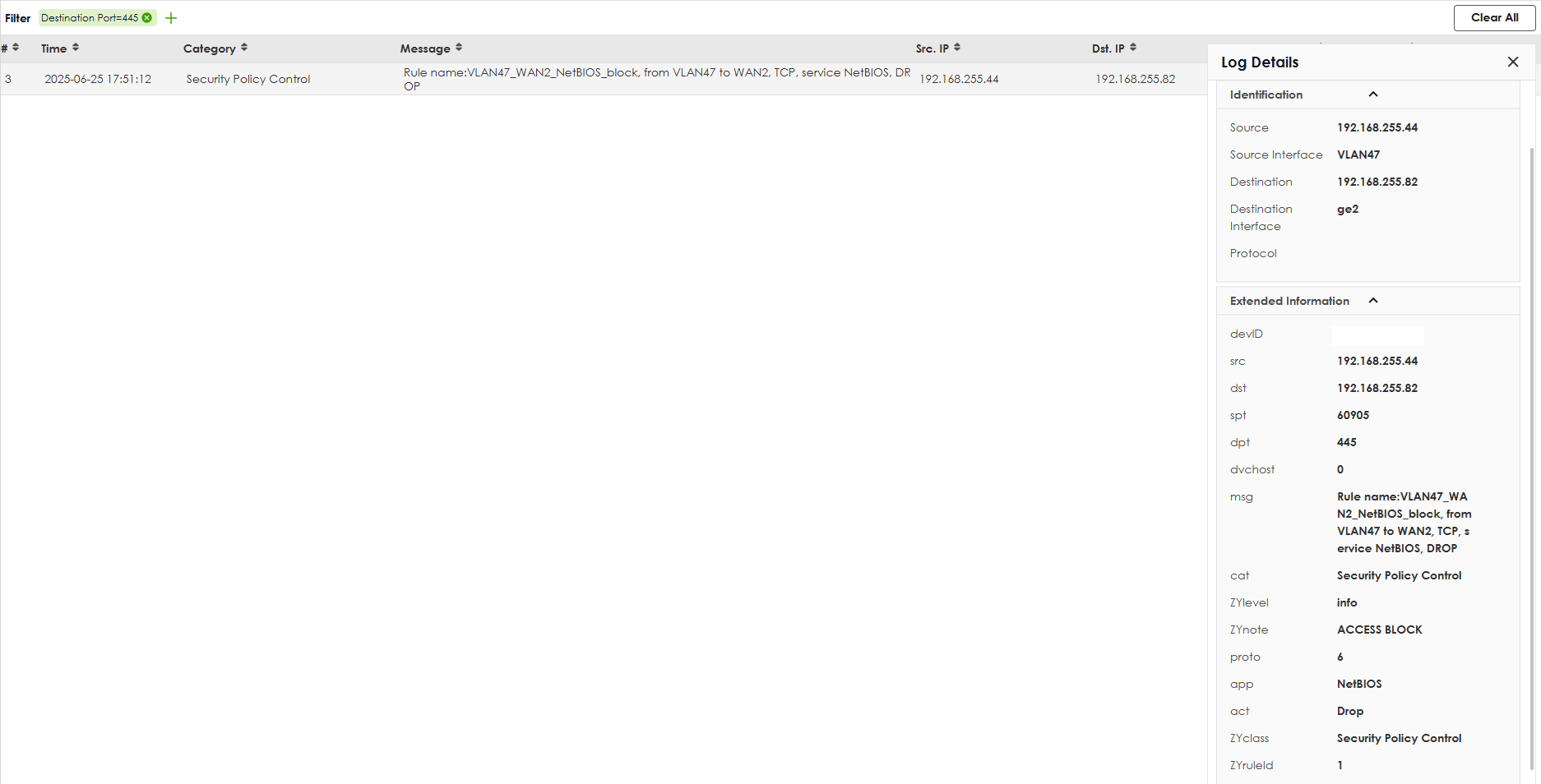
If I disable the NetBIOS block rule 1 it connects fine then when enabled blocks NetBIOS but its for to WAN2 which is not true as it is going down the VPN not out ge2 WAN2
0 -
Hi Melen,
I set up a test environment, confirmed this is still an issue, enabled Zyxel Support Access setting on the organization and created a local firewall user for you to check.
I messaged you the details as requested.
0 -
Can also setup test environment by test PC over teamviewer if needed too.
0 -
This is still a problem in V1.35 firmware
0 -
@Zyxel_Melen - Your last PM to my coworker @p4_greg on 7/16 contained a video showing these issues and I believe this was going to be escalated to development. As @PeterUK stated, we also confirmed this behavior is still present in 1.35. Please advise on a status or what else is needed from us.
0 -
Sorry for the delayed reply. We have addressed this issue, the police-based VPN traffic might be misrecognized as to WAN zone traffic and hit the security policy ANY to WAN. I will provide a date code firmware with you for 100H soon.
Hi @PeterUK
I will also provide you with the date code firmware for 200H, since the remote VPN issue is similar to this issue.
Zyxel Melen1 -
Messaged back. We are still in the same situation and this is not resolved.
0
Categories
- All Categories
- 439 Beta Program
- 2.8K Nebula
- 202 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.3K Security
- 515 USG FLEX H Series
- 328 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.3K Wireless
- 49 Wireless Ideas
- 6.9K Consumer Product
- 288 Service & License
- 458 News and Release
- 90 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.3K FAQ
- 34 Documents
- 85 About Community
- 97 Security Highlight
 Guru Member
Guru Member


 Zyxel Employee
Zyxel Employee