Vlan1 On Primary LAN Interface
 Ally Member
Ally Member


Hello,
I have a HUGE security concern about this topic and I am running a Flex USG500H and I spoke to tech support and discovered that I am not able to change the primary LAN interface (192.168.1.1) to any other vlan other then the default vlan1 and that is designed that way.
In my opinion that is a security "No No". This is what I was told by tech support that I am NOT able to change the primary Vlan1 from any other vlan of my choice.
If this is the case, please tell me I am wrong or if there is a way and what is the proper way / commands to do through the CLI or through the GUI so I can change this. I want to use another VLAN other then vlan1 as I like the flexibility and security. I would not turn vlan1 off, but it is nice to separate all networks out based on my needs and design my security needs based on that. Thank you.
Accepted Solution
-
This post can be officially closed out now. The issue lies within the limitation of the Zyxel Firewall not supporting a Native VLAN / PVID on a trunked interface port. Once I removed the the native vlan switchport from the trunked interface I then can move to the VLAN10 Interface / profile within the configuration on the firewall. Now it is working as expected. Thank you @Zyxel_Cooldia for all your support and assistance with this.
0
All Replies
-
Do you have a VLAN switch?
0 -
On current model you have a Native Ethernet thats no a VLAN but is untagged to which you can add VLAN that are tagged. On FLEX H models you can choice not to have a Native Ethernet and add VLAN that are tagged.
But I don't see your problem? On FLEX500 you can add a VLAN like 1001 and set the interface to 192.168.101.0/24 then on the Native Ethernet you can set the interface to 127.0.1.0/24 zone none to make it dead. Note if your going to do this make sure you don't lock yourself out the USG make sure the Zone for VLAN 1001 is the zone to want and that you have a from zone to Zywall then you need a VLAN switch setup to tag to to USG for VLAN 1001.
0 -
I do have a VLAN switch and have several Vlans on it, but on the primary interface LAN1 (192.168.1.1/24) for example you cannot tag a VLAN to it. There is no option to do that.
Can you post a config on what this will look like? I understand and do not want to lock myself out of it, but I was told by tech support this is NOT possible. I would want to configure VLAN10 to be native Ethernet (192.168.1.1/24). Can you post a sample config? Is that possible or do I need a whole new IP subnet?
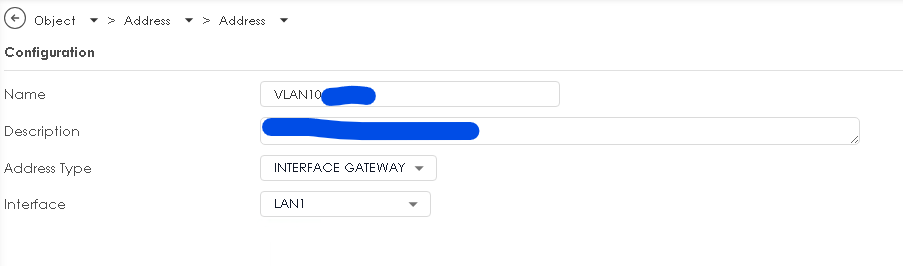
Would this config work? All I want to do is tag the primary Native Ethernet Interface.
Object-Address
Network-Interface
Internal Profile
I know I cannot have 192.1681.1/24 in VLAN10 as LAN1 profile has 192.168.1.1/24 in it so that is why I am lost on how this would look. What would I need to change or is this correct? I know I am probably missing something here.
Thank you.
0 -
The address object is wrong and needs to be removed in order to remove Native LAN1.
If you want 192.168.1.1/24 on VLAN10 you must first change Native Ethernet to like 192.168.99.1/24 then log in to 192.168.99.1 and add VLAN 10 with 192.168.1.1/24 then to be sure log to in 192.168.1.1 then remove Native Ethernet
0 -
This does not make sense.
How would I get rid of the native Ethernet (LAN1) interface when all my other Vlans are tied back to the LAN1 port profile? Isn't that profile (LAN1) actually tied to the physical Ethernet port? How can the VLAN10 profile be associated to the physical Ethernet port?
Can you please be more descriptive?
I do appreciate your help.
0 -
You have a FLEX500H which its setup to like a FLEX500 is different Of course with the FLEX500H if you don't want to remove the Native Ethernet you don't have to you can set to Unassigned but because 192.168.1.1 is what you login in too you be locked the USG so setup VLAN 10 with on another subnet then login to that subnet then Unassign Native Ethernet and then set VLAN 10 to 192.168.1.1/24
0 -
I am so sorry I am still not following you. I can tell you are the expert, but I might need you to simplify it for me. I am an intermediate user and understand the concepts but trying to understand how the physical interface will associate itself with the new VLAN10 that I have currently setup. The LAN1 profile, which is assigned to Ethernet P5 has the IP Address 192.168.1.1/24. When I disable that profile how would my VLAN10 profile know to route traffic through the physical Ethernet(P5) port without having the LAN1 profile available, which has the physical port assigned to it. It is not about deleting anything or disabling the LAN1 profile but understanding how the config looks without locking myself out, but how the configuration looks. Can you please provide me a small sample config, so I understand it? Screenshots will help out to illustrate this. Thank you very much for your help.
0 -
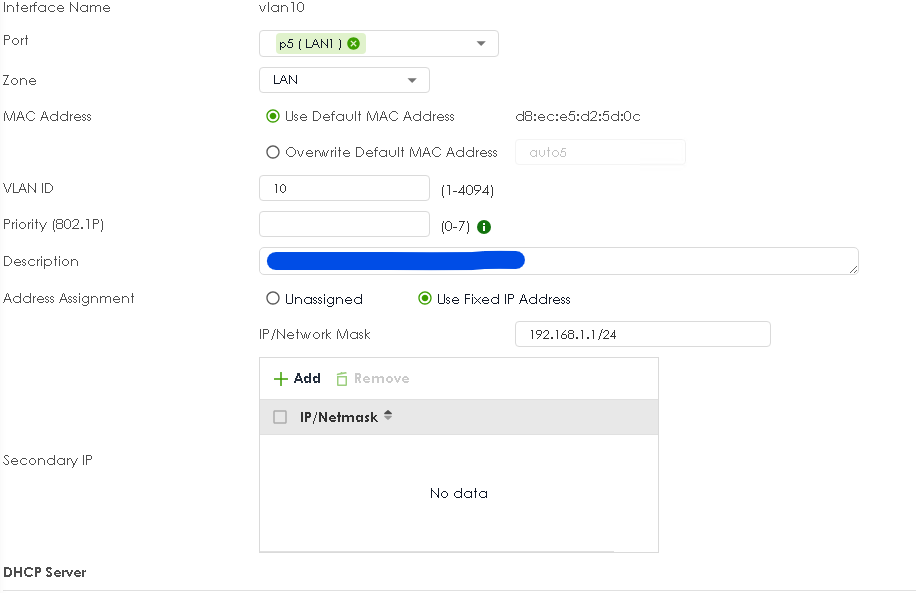
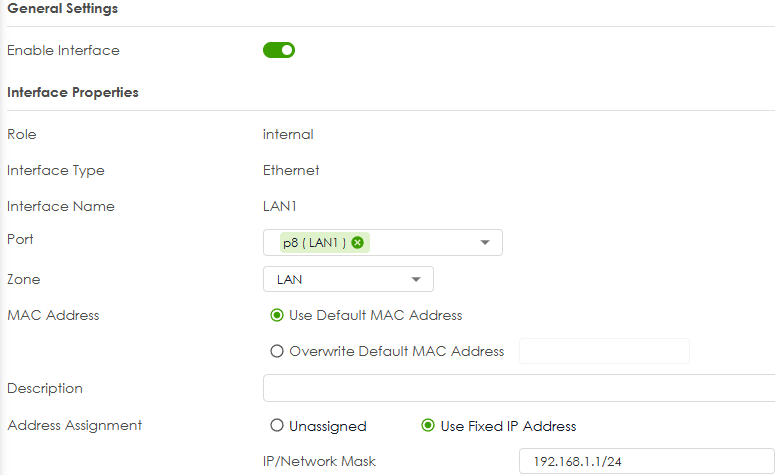
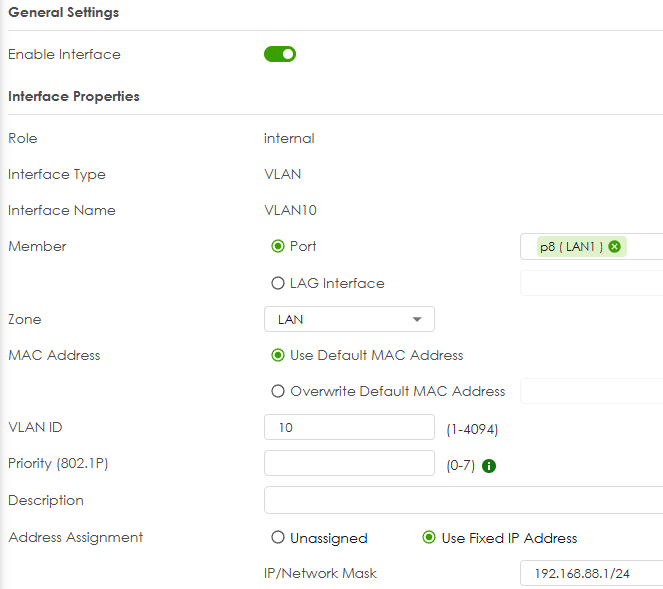
Ok so you have this (I use P8)
you then make VLAN10
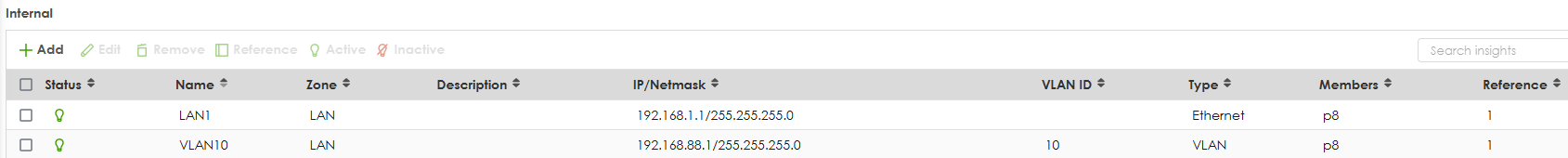
you have the following
then login to VLAN10 192.168.88.1 note your switch need to be setup to tag VLAN 10 out to USG
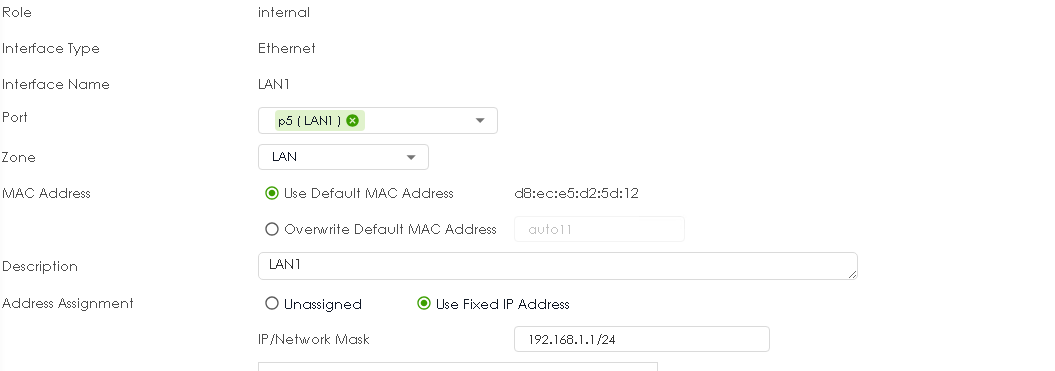
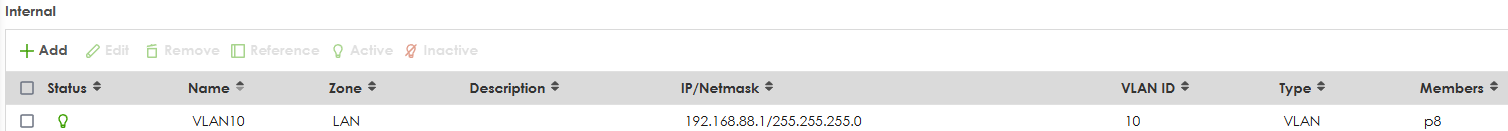
then you can remove Native Ethernet and have the following
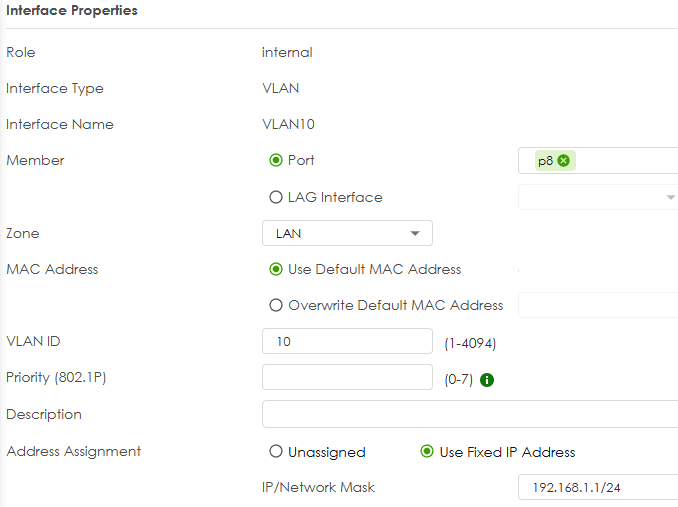
then set VLAN10 to 192.168.1.1/24
0 -
I did a test run and tried to reach the new ip of 192.168.88.1/24 on VLAN10 and was not able to reach it from another machine. Once you change it how am I supposed to log back into the VLAN10 interface. All my switches have been set to VLAN10 and that is there native VLAN. I just tried to ping the interface 192.168.88.1 and did not get a response and that is putting a static in my laptop NIC with the DG of 192.168.88.1. This is what confuses me.
If I set one of my laptops to 192.168.88.10 I should be able to ping 192.168.88.1 right?
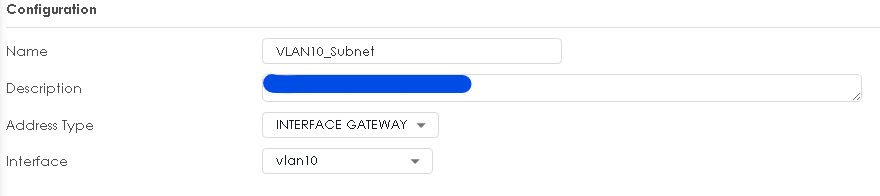
That is my backdoor to change the VLAN10 to 192.168.1.1/24. Is the below object set right. See below:
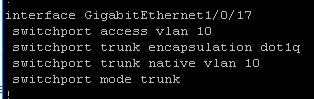
Here is the configuration of the port that the laptop is plugged into. So there should be no reason why I can not reach 192.168.88.1/24 as my DG for Vlan10. See below:
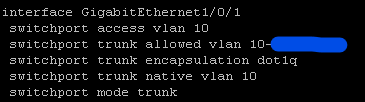
This is the port the USG Flex 500H is plugged into. See below:
This is why I get confused with this firewall. I understand how it works, but this firewall is a little convoluted IMO. Thank you.
0 -
What is your switch?
If you set your laptop NIC to VLAN 10 this will be tagged then connect direct to the FLEX port for VLAN10 and you be able to access it.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Guru Member
Guru Member