Vlan1 On Primary LAN Interface
All Replies
-
Hello…..I did exactly what you said and followed the instructions, and you were right I was able to connect, but one problem I could not get out to the internet at all. I could get into my equipment from the VLAN10 interface (Internal LAN), but once I rolled back to LAN1 interface it all started working just fine. I have a Cisco switch. I am telling you it is this device and how it is setup. I am currently rolled back to the LAN1 interface profile, but you are correct the VLAN10 Interface works as you put it, but no internet no way to get out to the outside world. I did change the Object Under Address from interface subnet or Interface gateway for vlan10 and if I changed it to interface gateway I could not get to 192.168.1.1/24 form VLAN10 and had to do it from another VLAN that I have setup. Does that need to be deleted or does that get attached to the zone? I have always had issues with the primary interface of this firewall and confused. This is where I am confused. What is the correct configuration? I like your illustration and did follow it and had to reboot the firewall a couple times. Thank you.
0 -
You likely need a routeing rule for the VLAN10 to next hop WAN plus policy rule then you should get internet.
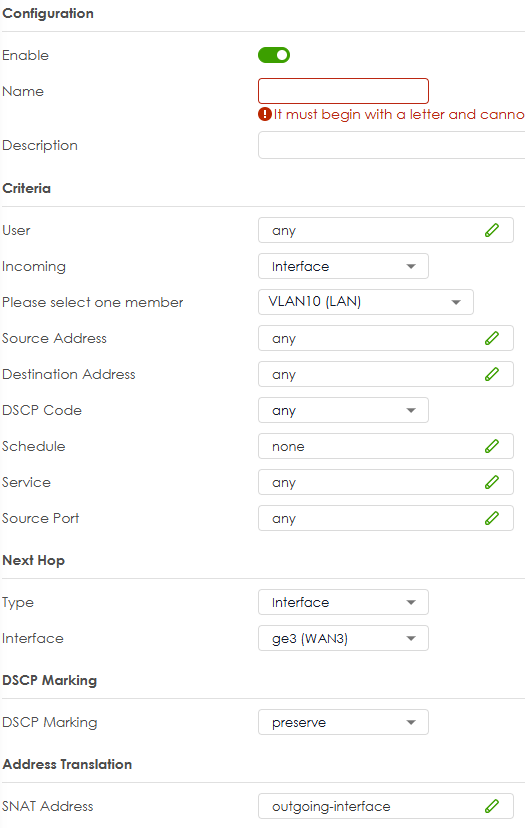
The Address Object is used for like policy control rules by itself does nothing in this case with Interface subnet it pulls what subnet that gateway is on so for VLAN10 its 192.168.88.0/24 if that what it on if when you change the interface IP/subnet the Address Object updates so if when making a policy control rules you can have
from LAN
to WAN
source Address Object Interface subnetdestination any
service anyas for the routing rule not static route
incoming VLAN10
next hop interface WAN
other options can be left as is
0 -
How do I set that up? I am newbie when it comes to this thing. This is where proper instructions would help. I am just providing feedback. What does the Object - address? Is it the interface_subnet or interface gateway or should I delete it? This is again where I am lost. Can you please provide screenshots again? Is it a static route or a policy route? I have four other VLANS is there anything else I need to do to those and one guest VLAN that does not have access to the other VLANS and strictly goes out to the internet.
0 -
edited my post above
0 -
Thanks. In your post above is that under policy control or policy route. Is that two different rules or one rule? Should the object be set to interface gateway or interface subnet?
I have four other VLANS is there anything else I need to do to with those and one guest VLAN that does not have access to the other VLANS and strictly goes out to the internet. All the other VLANS go out through the LAN1 or this new case would be VLAN10. I want to make sure there is nothing else I am missing here.
Being honest I am still confused. Can you please do screenshots? Your screenshots really did help. Thank you.
0 -
Just to update you list Interface gateway not Interface subnet so one pull just the gateway IP the other the subnet range.
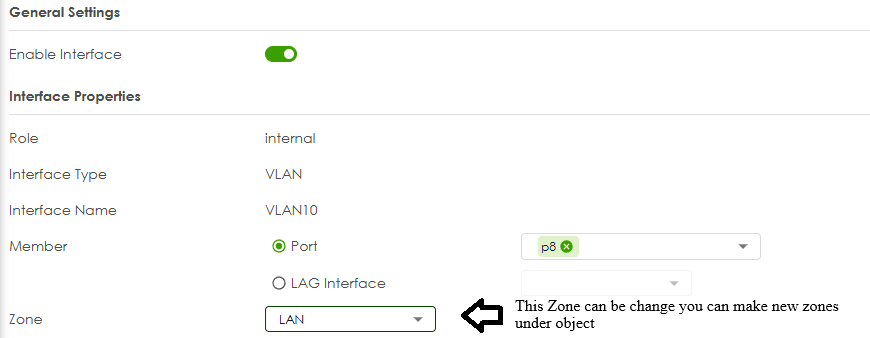
You can make zones and set them when you make the interface to isolate different LAN/VLAN note you may have the default policy control rules that allow more then what you want so review them.
0 -
I am still confused and do not understand.
Issue 1:
I have VLAN10 setup for the internal network. All equipment / nodes can talk to each other when on VLAN10 (Internal Network, but I cannot get out to the internet unless I rollback to LAN1, which is where I am currently at.
Issue 2:
I have four VLANS 2,3,4, and 100 other that need to talk to each other and require internet as well. Will VLAN10 once setup correctly provide me no issue and work as expected?
Issue 3:
I have one VLAN that needs to be segregated from the other VLANS and just needs to get out to the internet. Will VLAN10 once setup correctly provide me no issue and work as expected?
Issue 4:
What is address - object supposed to be set too? Interface Gateway or Interface Subnet?
How do I fix these issues? Can you please provide screenshots? Maybe this post will help someone else in the future. This is again so convoluted and needs to be simplified. Everything in the current state right now works as I want it too, but I want to setup VLAN10 as the source for my Default-Gateway, which right now LAN1 is my Default-Gateway.
I am so sorry, but everything above is so confusing when you do not illustrate it better. Thank you.
0 -
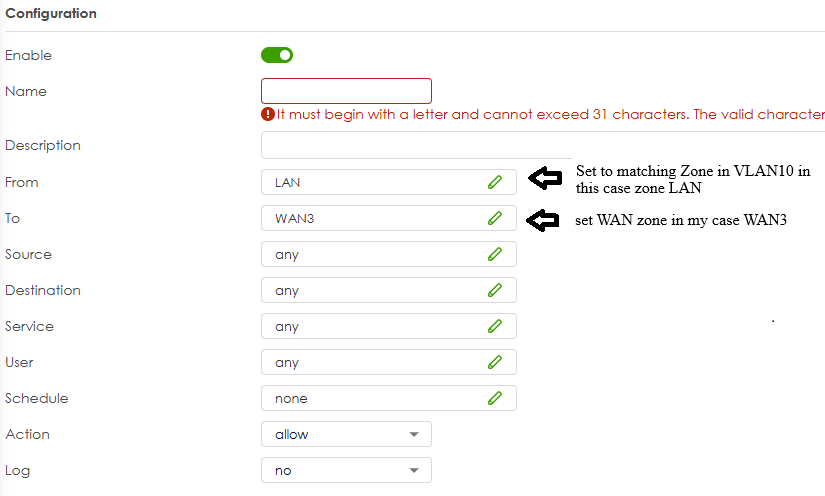
For get out the internet on VLAN10
routing rule note my next hop is WAN3 but set this to your WAN
policy control rule note if DNS is to gateway make another policy control from LAN to Zywall
here you can set the zone
If you have more subnets by VLAN you need to make more VLAN and give them there own subnet and Zone if needed.
0 -
Does this fix all my issues? I do appreciate it and I will create this for VLAN10, but does this solve my other issues 2,3, and 4 that is why I lined it all out. As mentioned before everything works correctly under LAN1 Interface. Why does the LAN group not work for this VLAN10 Setup?
Why does LAN1 profile just work out of box? I thought this is what Zywall zone / profile is supposed to be? Why do I need to change the zone from LAN when that is the default zone and should forward all the traffic as required?
I still did not get the answer to Issue 4.
0 -
Does this switch of yours have a GUI?
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Ally Member
Ally Member


 Guru Member
Guru Member