Remote Access IPSEC VPN doesn't work
 Freshman Member
Freshman Member

Hello,
I did setup Remote Access IPSec VPN using SecuExtender. I can't make it work. To troubleshoot I connected the client directly to the wan network of the USGFlex200 (192.168.250.50/24) . Here is attached the SecuExtender console output. I'm a new Zyxel user, so I probably have missed something obvious in the configuration (even if I used the wizard) ?
Thanks in advance,
Best regards,
Jerome
Best Answers
-
So you enterer the VPN settings manually in SecuExtender?
0 -
Hi Peter - thanks so much for this detailled answer !
I did all of that - but you know what - I'll restart from scratch and will let you know.
Do you know if there is a way to use pre-shared instead of certificate for remote access (it should as you have this option in SecuExtender) ? Where do you configure the pre-shared on the GW side ?
Thanks again,
Have a good day
0
All Replies
-
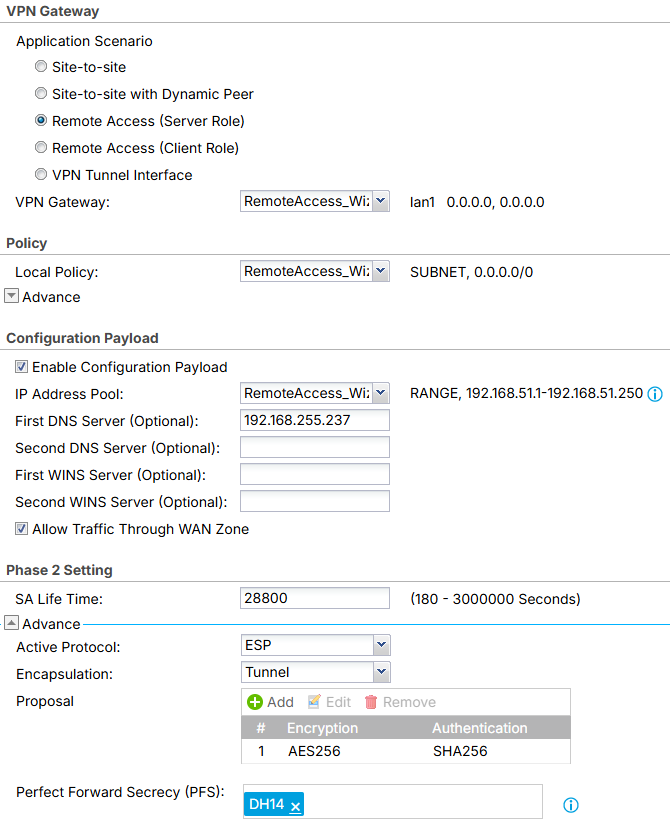
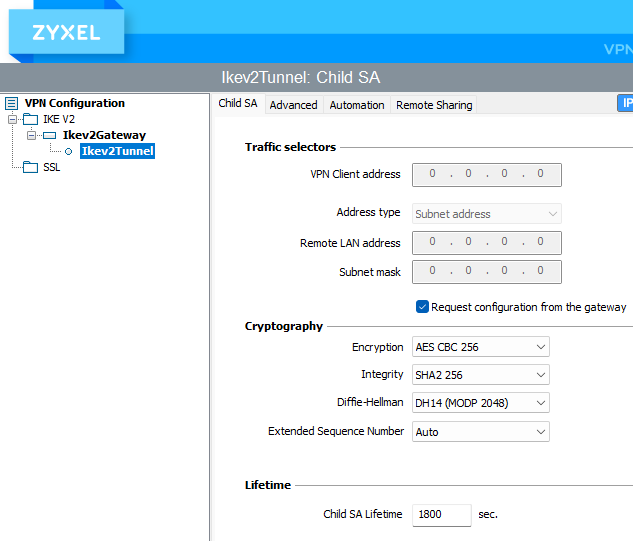
With the wizard did you select IKEv2?
0 -
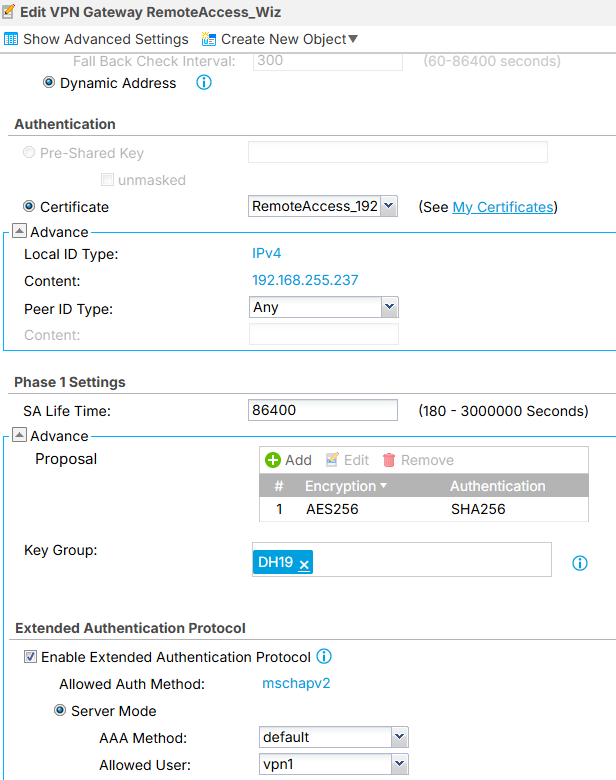
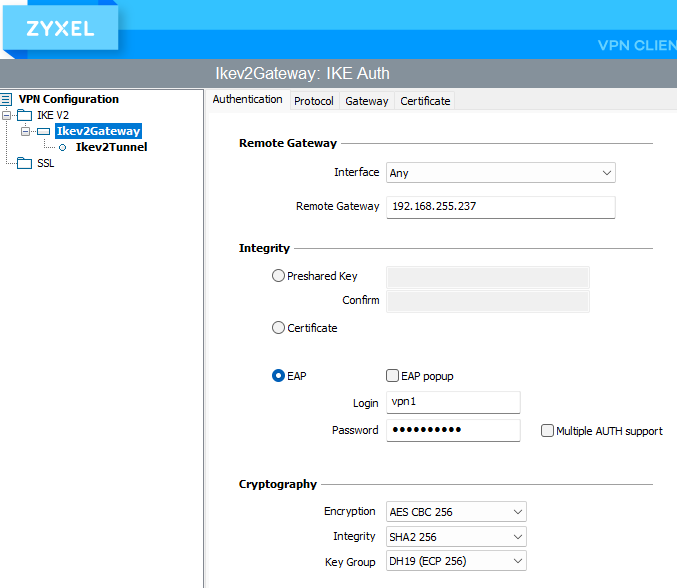
Yes IKEv2. Wizard screenshots attached.
0 -
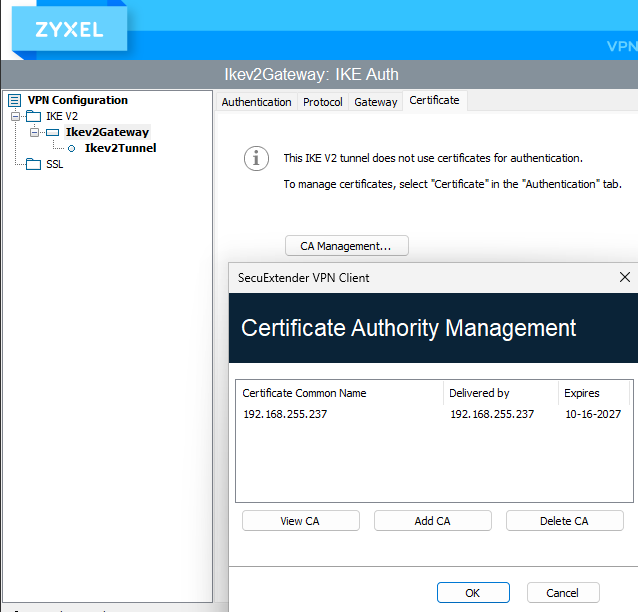
Log are saying Self-signed certificate not accepted, on SecuExtender are you using the "get from server" under configuration?
0 -
Hi @Jerome89,
Welcome to Zyxel Community!
After analyzing, your USG FLEX is using a self-signed certificate with a private WAN IP.
Since this is not a public IP, the VPN gateway is likely behind another router, causing the certificate validation and IKEv2 negotiation to fail.
Please check the following:
- Make sure the USG FLEX has a public IP or that UDP ports 500 and 4500 are forwarded from the upstream router.
- Use a certificate whose CN matches the public IP used by the client.
The VPN should connect if the gateway is reachable on a valid public address.
Zyxel Tina
0 -
Yes I tried this during my tests, without really understanding what it was suppodes to do. I guessed it was a way to get the VPN RAS Setup from the GW ; anyway it failed.
0 -
Hi Tina,
Thanks for your answer.
You're right my Zyxel is behing a NAT router. But as it didn't work, in order to isolate issues & troubleshoot, I did put the client computer with SecuExtender on the same network as the wan1 interface ⇒ Client and GW are on the same Net, so no NAT is involved. So for this test, configuration (including self-signed certificate) should be consistent (?). Would it be smarter to try with the edge_certificate for testing purpose ?
Question : In SecuExtender, Configuration/Wizard menu, IKEv2, in the 2/3 menu it's asking for a shared key or a certificate (to authenticate the GW I guess). If using a shared key where is it configured on the GW (I'm only using Remote Access VPN, no site-to-site) ? (Just to try with pre-shared instead of certificate)
Thanks in avance,
All the Best,
Jerome
0 -
So you enterer the VPN settings manually in SecuExtender?
0 -
Hi Peter - yes I entered them manually using the wizard.
0 -
(Sorry the thread is still opened - I closed it by mistake - is there a way to mark it unansered ?)
0 -
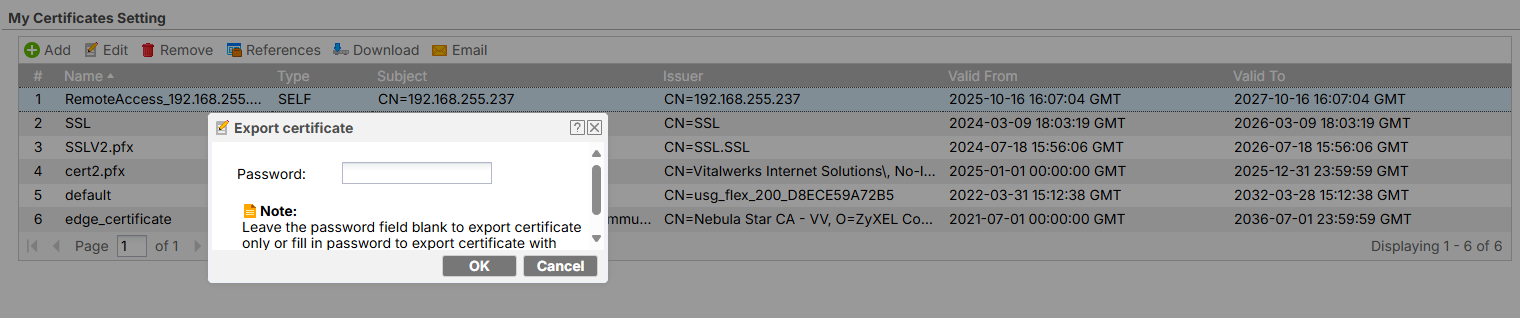
In which case you need to download the certificate USG made to the SecuExtender
copy gateway setting to SecuExtender
download certificate without a password
added to certificate SecuExtender
copy VPN tunnel setting to SecuExtender
For the VPN to work by WAN as you are behind NAT you need to make a certificate with that WAN IP and set it to be used in VPN gateway setttings and SecuExtender.
0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 216 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.4K Security
- 570 USG FLEX H Series
- 343 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 6.9K Consumer Product
- 295 Service & License
- 471 News and Release
- 90 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.7K FAQ
- 34 Documents
- 87 About Community
- 102 Security Highlight
 Guru Member
Guru Member


 Zyxel Employee
Zyxel Employee