How to Use Two Factor with Google Authenticator for VPN Access?
 Zyxel Employee
Zyxel Employee



How to Use Two Factor with Google Authenticator for VPN Access?
In previous firmware versions, USG supports pin code by SMS/Email as two-factor authentication method. However, SMS-based two-factor authentication is not safe. Compared to SMS-based method, Google authenticator is the most secure method to receive verification code for 2-factor authentication. Google authenticator gives a new code every 30 seconds, so each code expires in just 30 seconds which make it a secure option to generate codes for 2-step verification. Furthermore, Google authenticator is free to download, easy to use, and is able to work without Internet. This example illustrates how to set up two factor with Google Authenticator for VPN access.
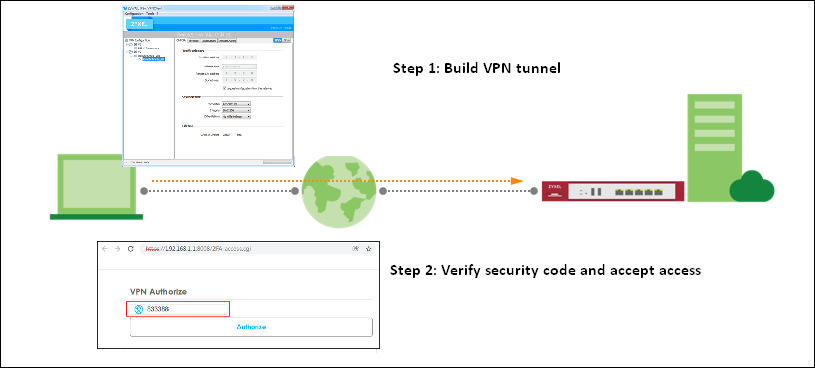
Two Factor with Google Authenticator Flow
1. Enable Google Authentication on user
2. Set up Google Authenticator
3. Configure valid time and login service types
Enable Google Authentication on user
Select a VPN user and switch to Two-factor Authentication tab.
CONFIGURATION > Object > User/Group > User, create a new user
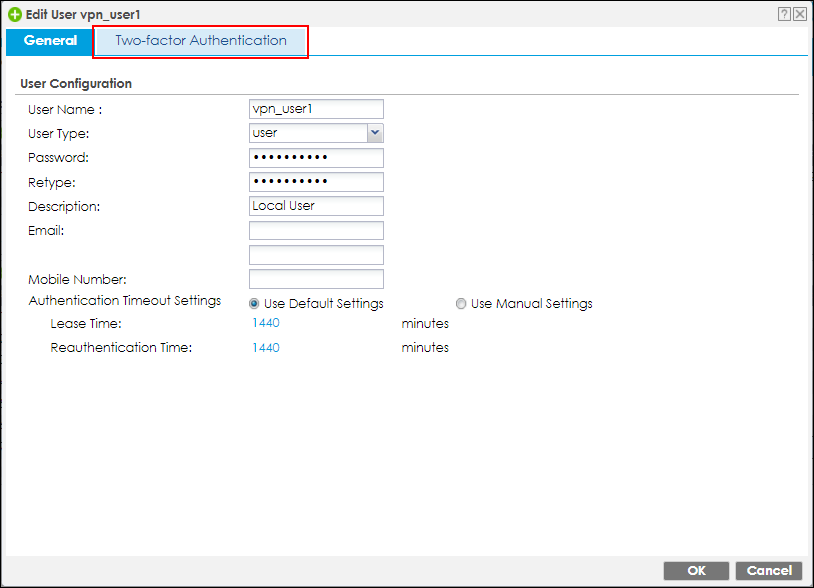
Enable Two-Factor Authentication for VPN Access checkbox.
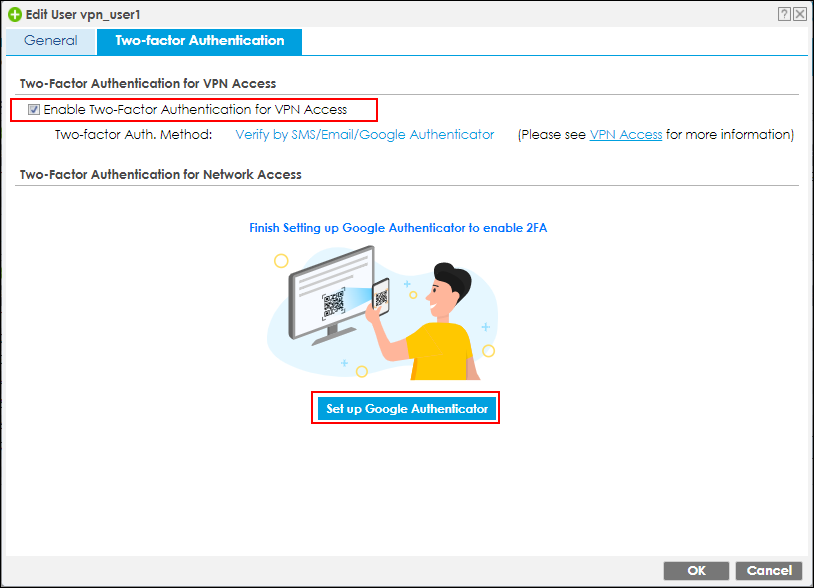
Set up Google Authenticator
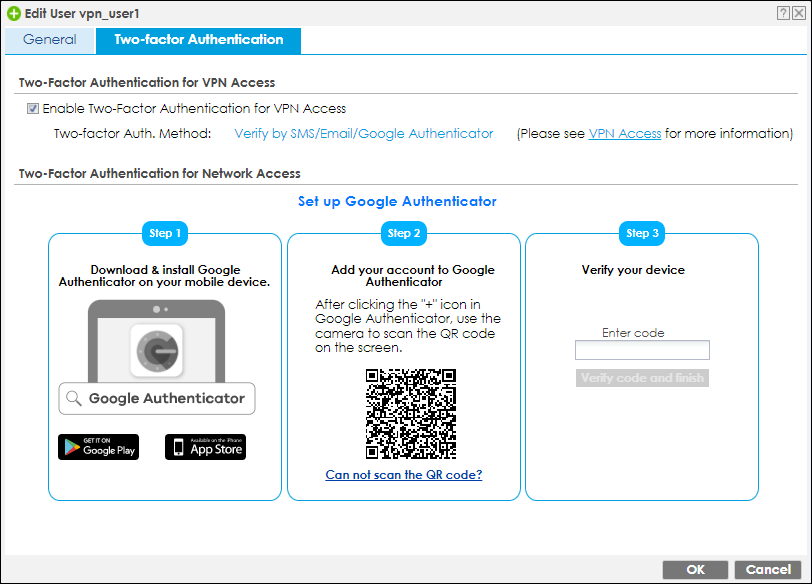
1. Download and install Google Authenticator on your mobile device.
Apple Store
Google Play
2. Register the VPN user account to Google Authenticator. Open Google Authenticator App and scan the barcode on Web GUI.

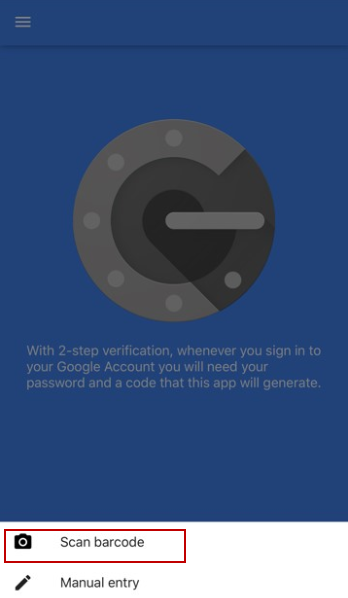
3. Enter the token code which displays on Google Authenticator to “Step 3” and click “Verify code and finish” to submit and verify the code.


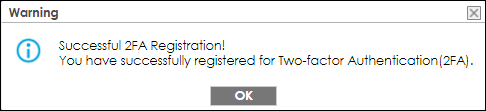
The pop-up window message informs the verification result.
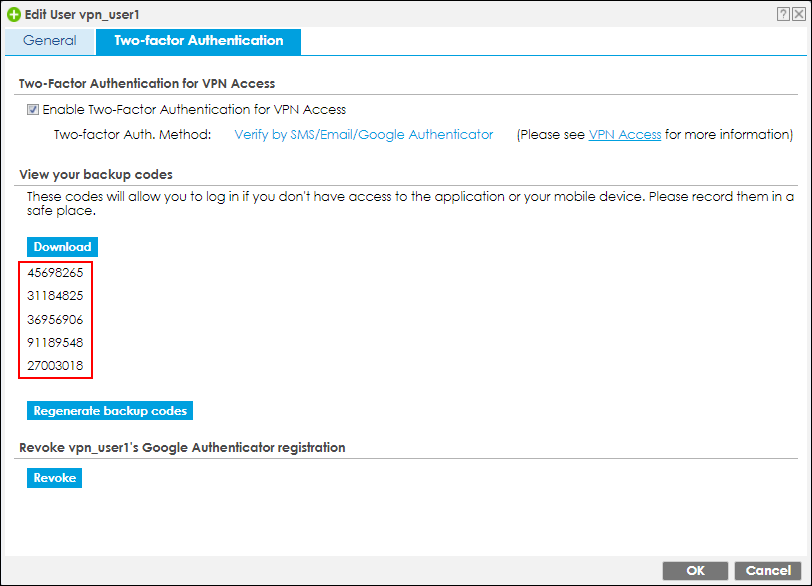
4. After 2FA registration is set up successfully, there are backup codes on web GUI. The backup codes are for device login in the case you don't have access to the application on your mobile device. Download the backup codes and record them in a safe place.
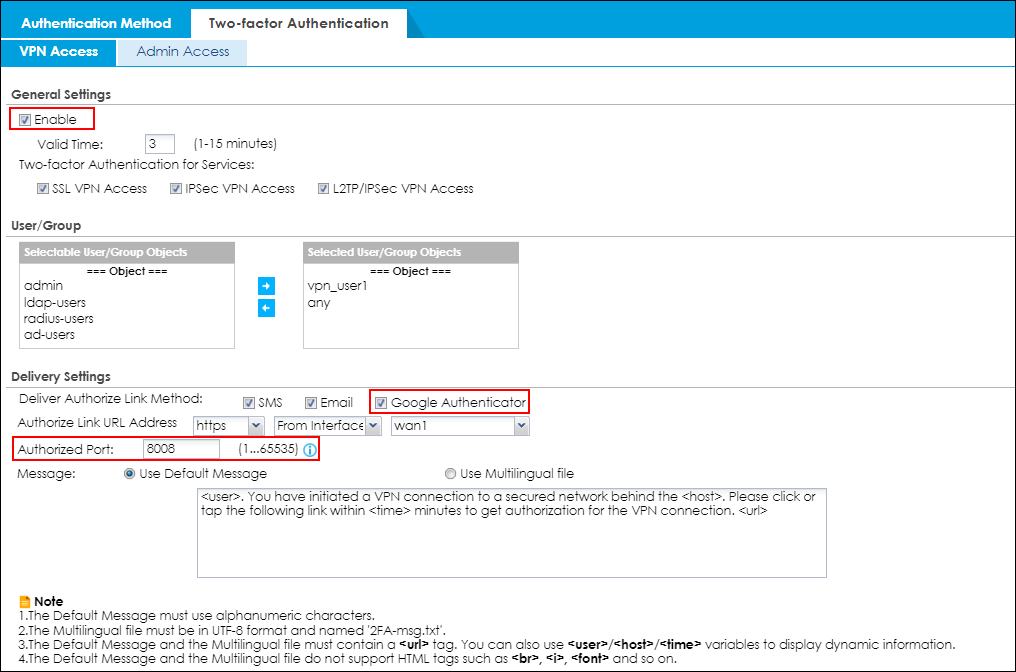
Configure valid time and login service types
Enable two factor authentication for VPN access. Configure valid time and select which VPN types require two-factor authentication for VPN user. The valid time is the deadline that user needs to submit the two-factor authentication code to get the VPN access. The request is rejected if submitting the code later than valid time. By default, the valid time is 3 minutes. The authentication page is working on specific service port. After building up VPN tunnel, user have to enter the code in the Web GUI.
Test the Result
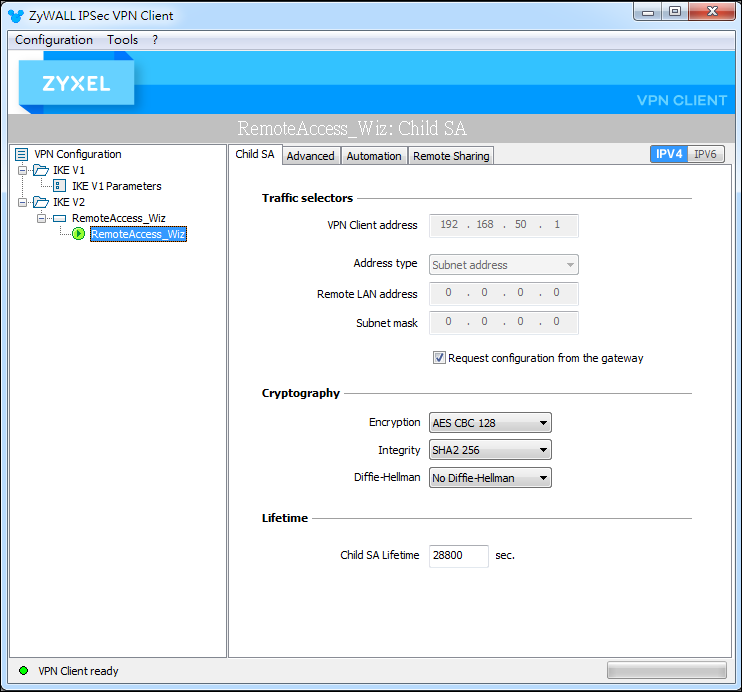
1. Build VPN tunnel on Zyxel VPN Client.
2. Browser will pop up authentication page to enter the verification code.
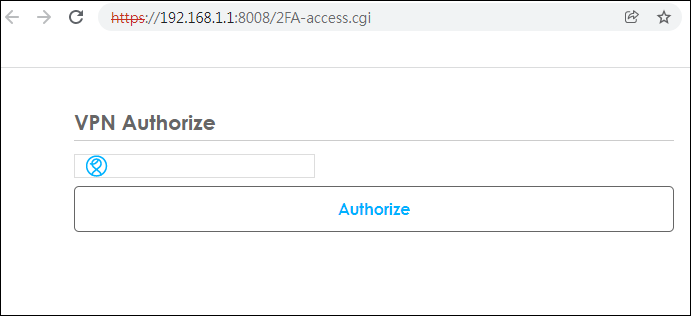
3. Enter the code shown on Google Authenticator and click "Verify". You can also enter the backup code if you don’t have mobile device on hand.


4. Enter the code shown on Google Authenticator and click "Verify". You can also enter the backup code if you don’t have mobile device on hand.

What Can Go Wrong
1. Default Authentication service port is working on 8008 port. You can customize it to others. Of course you have to allow service port (to Zywall) in your Policy Control rule.
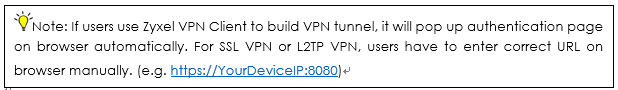
2. Zyxel VPN Client will pop up authentication page automatically on browser. If you build VPN tunnel by SSL VPN or L2TP VPN, you have to enter correct URL for enter verification code.
3. No matter SMS, Email or Google Authenticator are enabled, one of three types is verified then VPN user is authorized.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 603 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight