Remote Access VPN Wizard for SecuExtender IPSec and Non-SecuExtender IPSec VPN Clients
 Zyxel Employee
Zyxel Employee



With USG FLEX/ ATP( since ZLD 5.20) you are able to provision predefined settings on your device to SecuExtender IPSec as well as non-SecuExtender IPSec VPN clients. This article will show you how to use Remote Access VPN Setup Wizard to quick setup VPN tunnel using IKEv2 with EAP-MSCHAPv2 authentication.
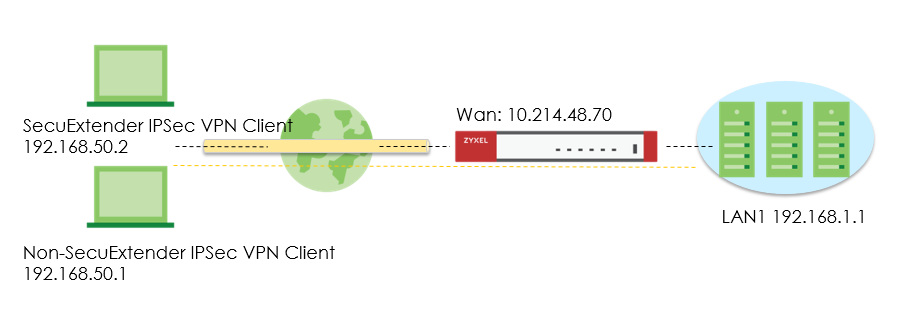
Set up VPN Tunnel on ATP/USG FLEX
1.Log in to the Web GUI of your USG-FLEX/ATP, click Quick Setup, then select Remote Access VPN Setup to build up VPN tunnel with the Wizard.

2.Select Remote Access VPN Setup, and choose Zyxel VPN Client (SecuExtender IPSec).

3.Configure the VPN Authentication Method
(1) Choose Incoming Interface
(2) Choose Certificate for VPN Validation
(3) Select the tunnel type Full Tunnel and enable the check box of Allow Client VPN Traffic Through WAN.

4.Configure the IP Address Pool for the client
The IP address pool will auto select non-used subnet on the device to avoid setting up the same subnet on the device. The IP address Pool will begin at 192.168.50.1
If the subnet 192.168.50.1 exists in the gateway settings, the IP address pool will automatically change to 192.168.51.1 subnet.


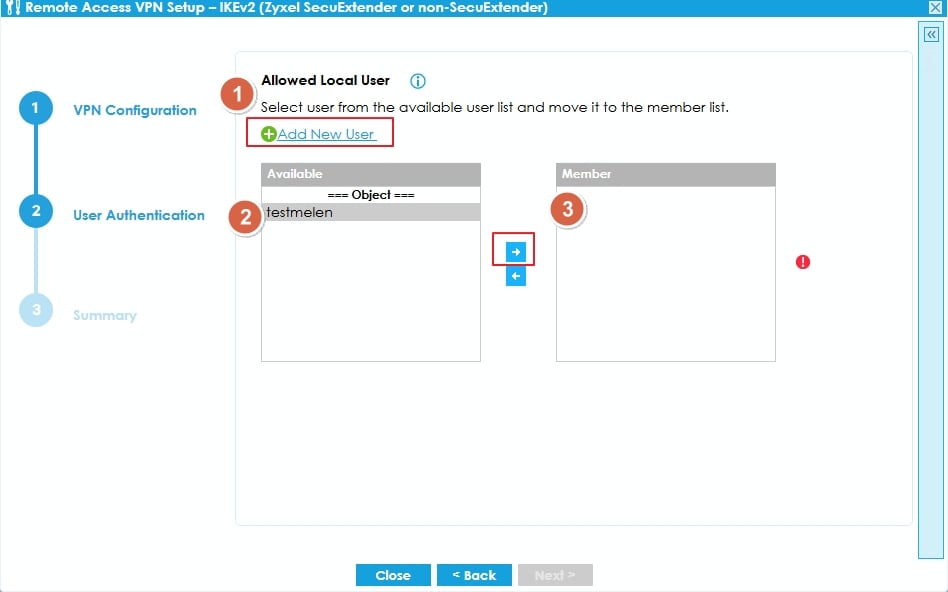
6. After done all the steps in the wizard, you can choose using either SecuExtender IPSec or non- SecuExtender IPSec VPN clients (iOS/MacOS, Windows, Strongswan-Android) to provision the VPN settings
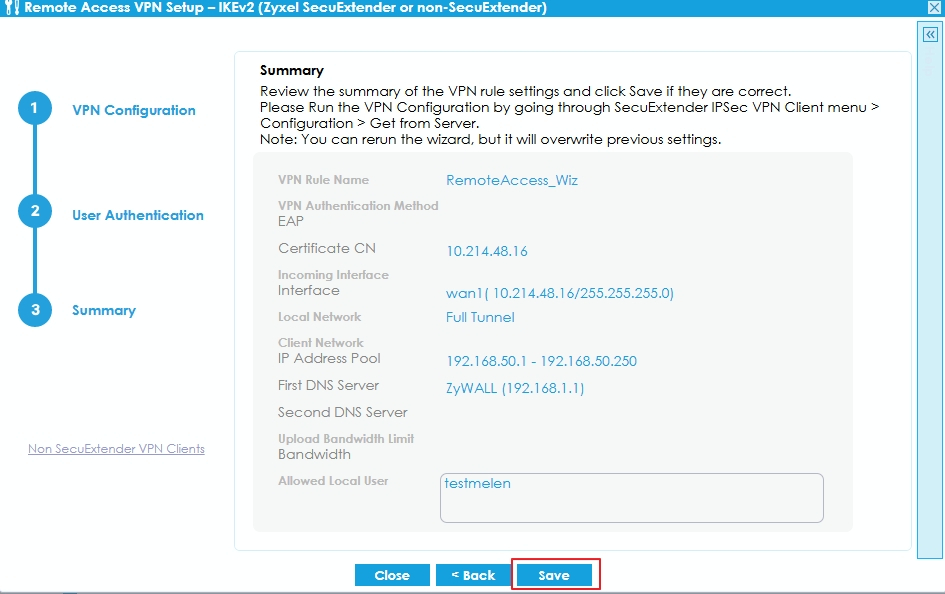
- SecuExtender IPSec VPN client: Click Save button to complete the Wizard
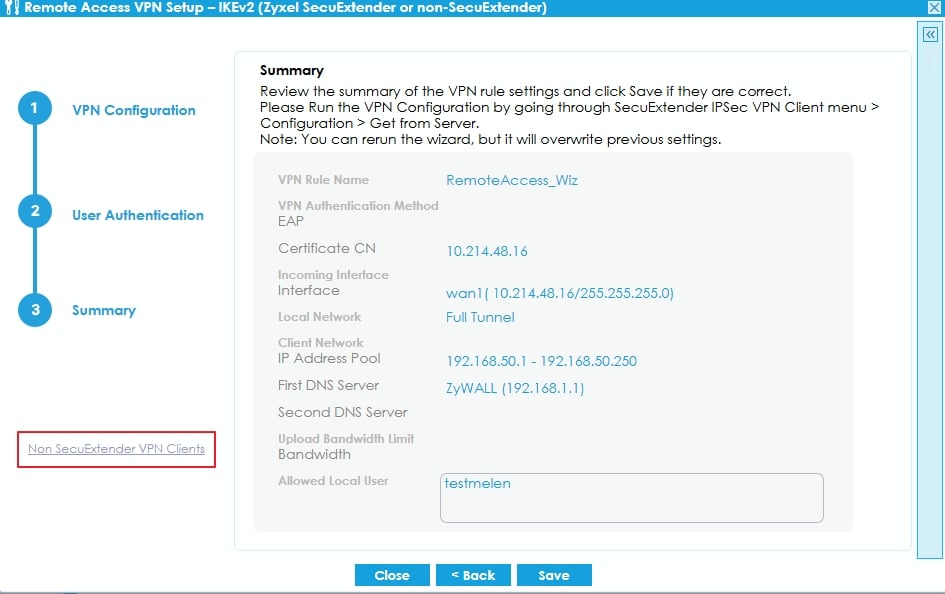
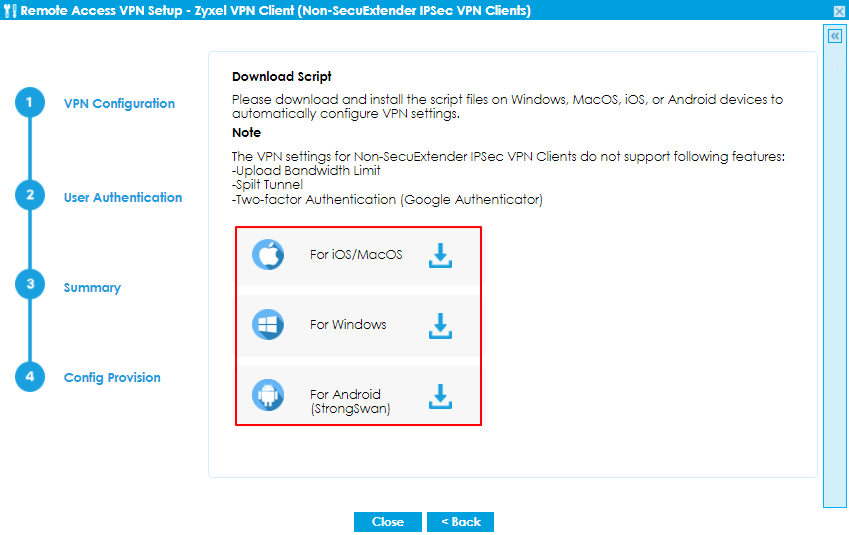
- Non-SecuExtender IPSec VPN client: Click to Non-SecuExtender VPN Client at the left hand side, then choose which device’s operating system you want to download the script to install on.
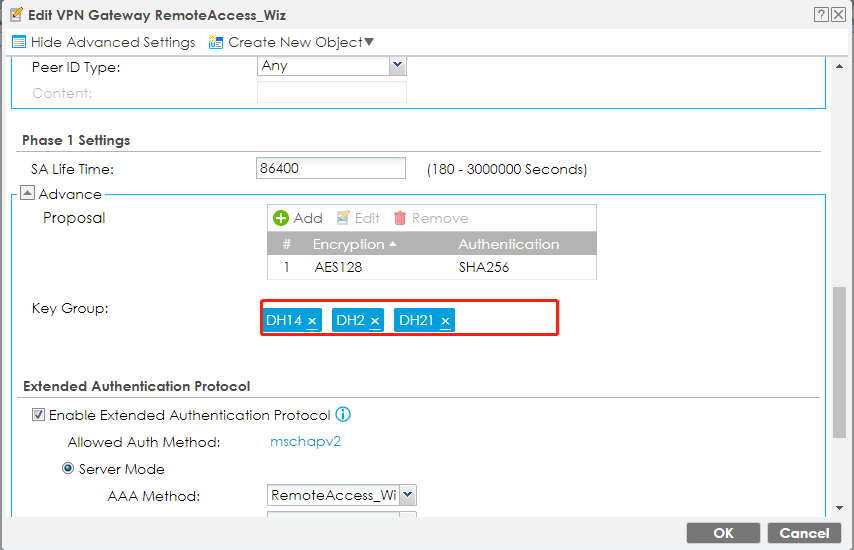
7. (Optional) Since ZLD5.10, Remote Access VPN Setup Wizard uses DH group 14 for VPN phase 1 setting. If you are using perpetual SecuExtender IPSec VPN client with default DH group 2, you can also manually add more DH group on ATP/USG FLEX to avoid re-provisioning. You can add maximum of 3 DH groups. ·On ATP/USG FLEX Web GUI, go to CONFIGURATION > VPN > IPSec VPN > VPN Gateway, edit the RemoteAccess_Wiz. In Phase 1 Settings, you can add more Key Group (DH)

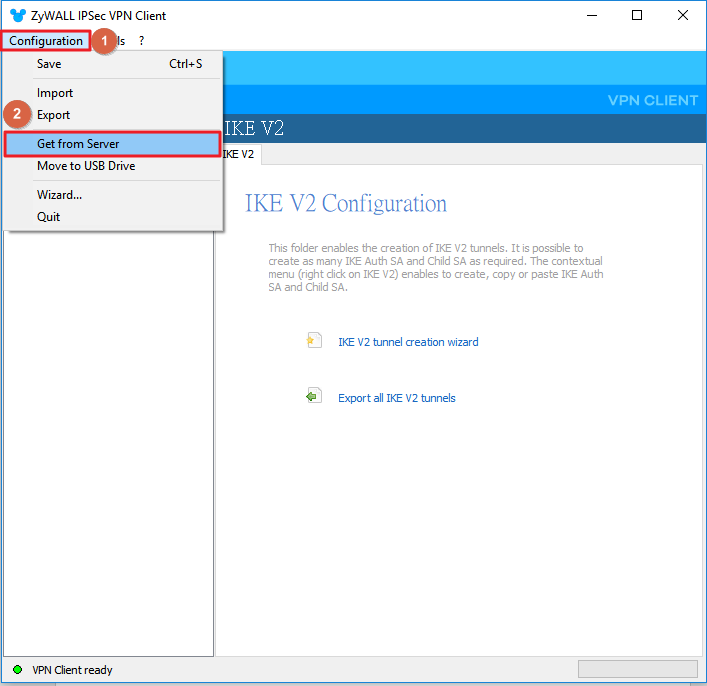
Test the result For Windows SecuExtender IPSec VPN client:
1. Go to Configuration tab, and click “Get from Server”
2. Enter gateway IP and credential to get provision file from gateway.
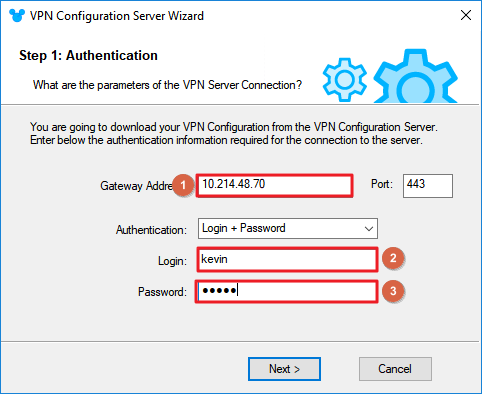
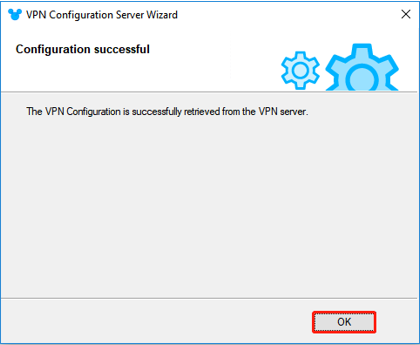
Click “OK” to finish.
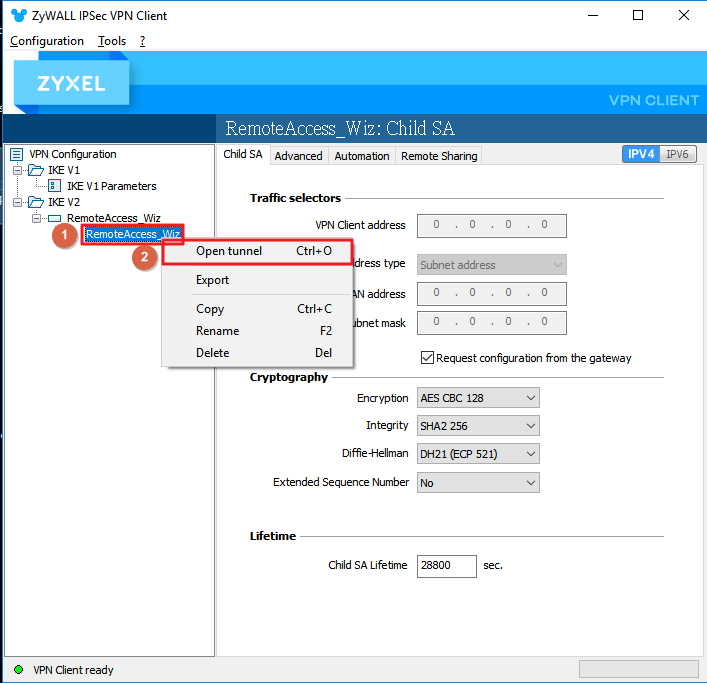
3. Click “Open tunnel” to build up VPN connection.
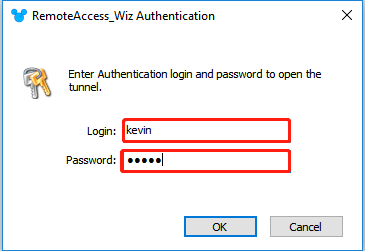
Enter credential and click “OK”.
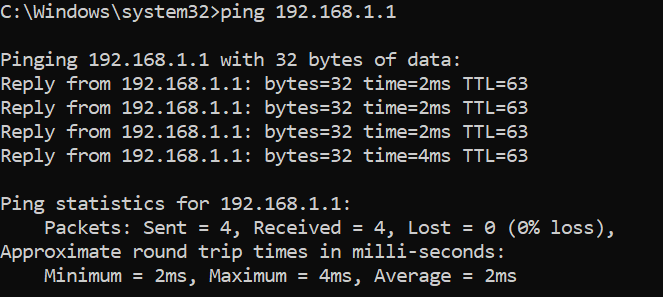
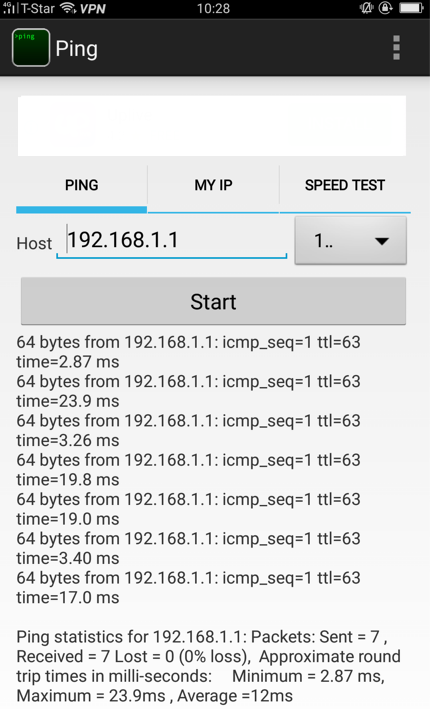
4. The remote user can ping the internal network now.
For Windows native IKEv2 client: 1. Extract the Script File, perform the script as Administrator.

2. VPN for Native IKEV2 is created successfully.
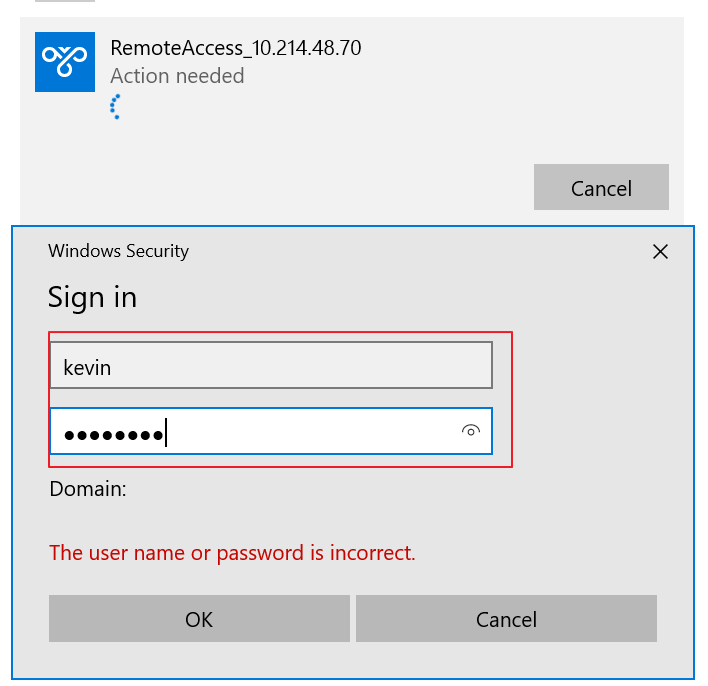
3. Enter the VPN credential to complete the connection.
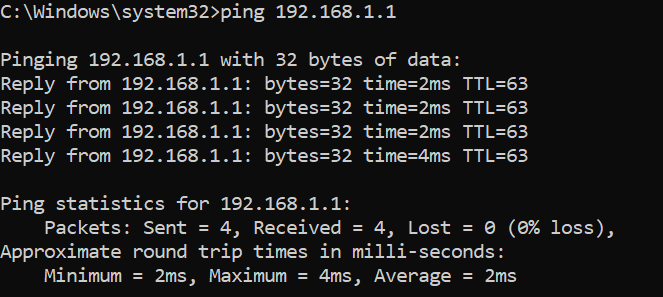
4. The remote user can ping the internal network now.
For iOS/MacOS: 1. Send the Script to Device via email in example, then download the file
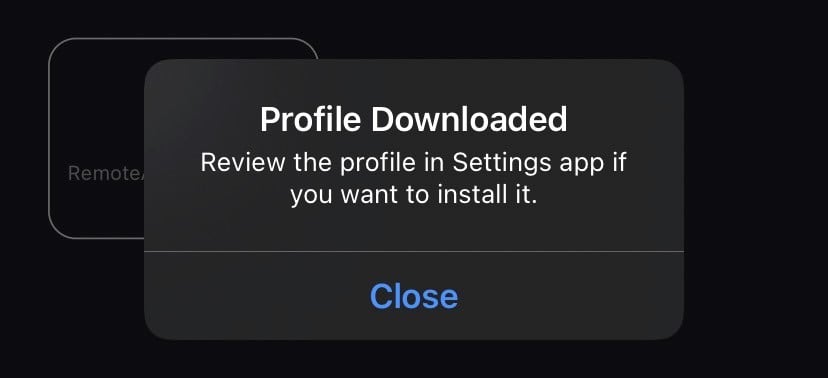
2. Settings->Profile Downloaded
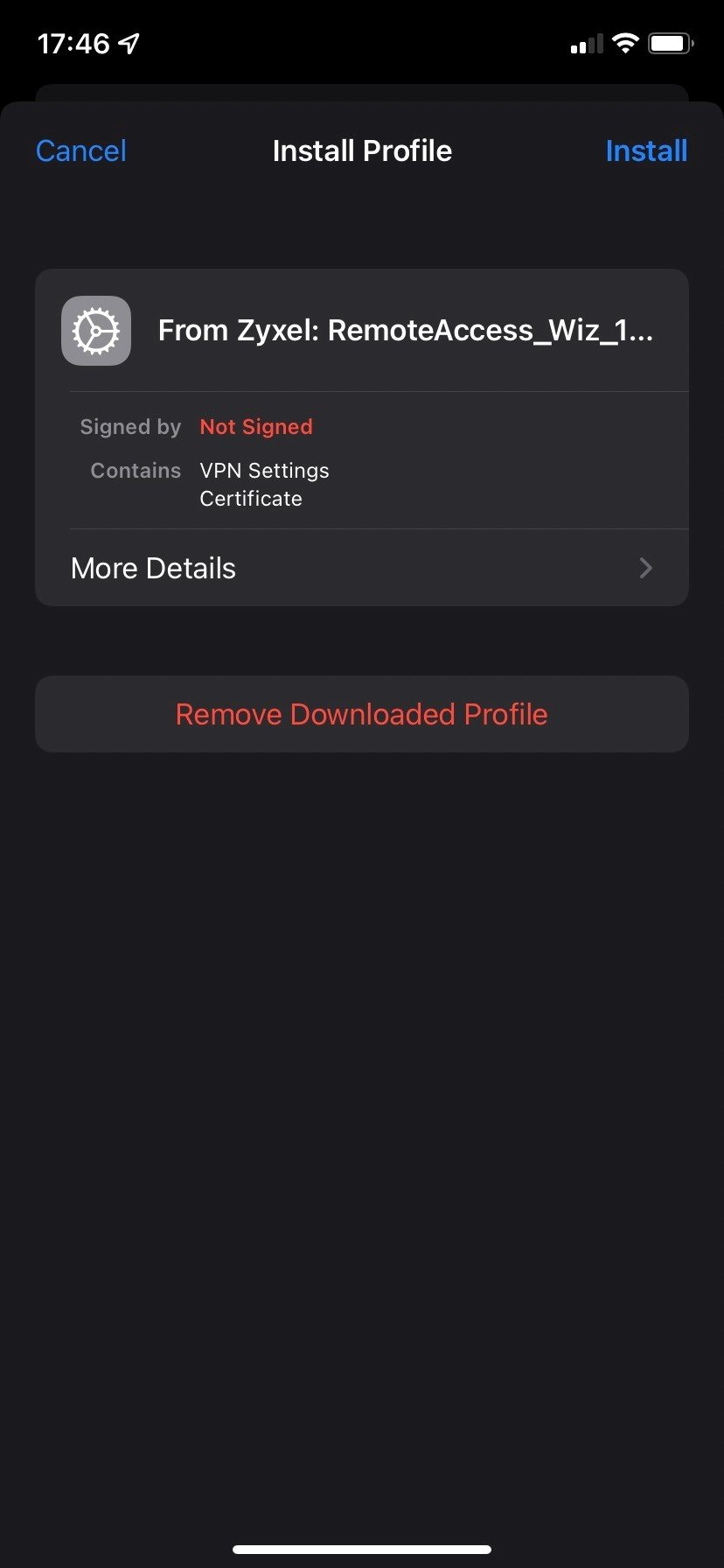
3. Press Install
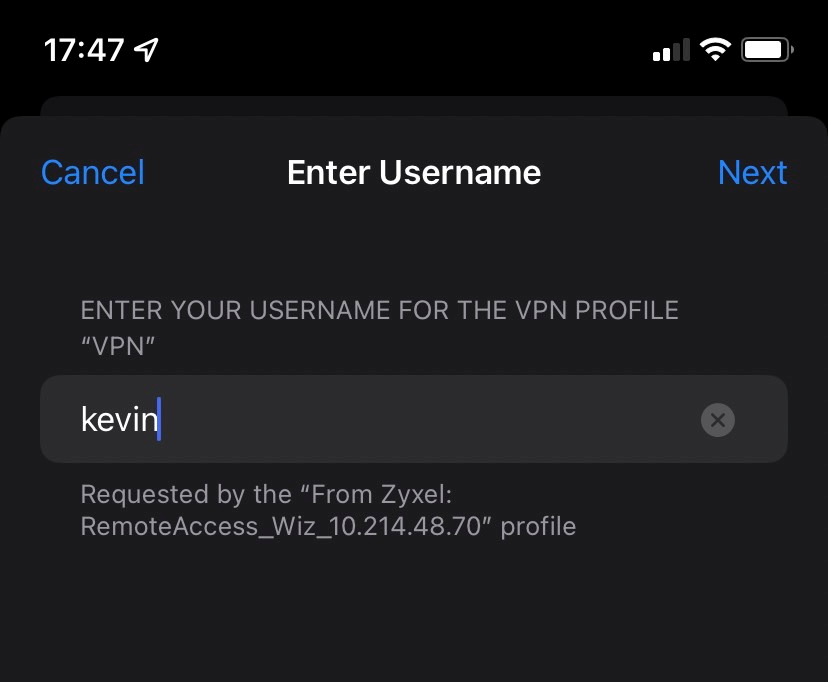
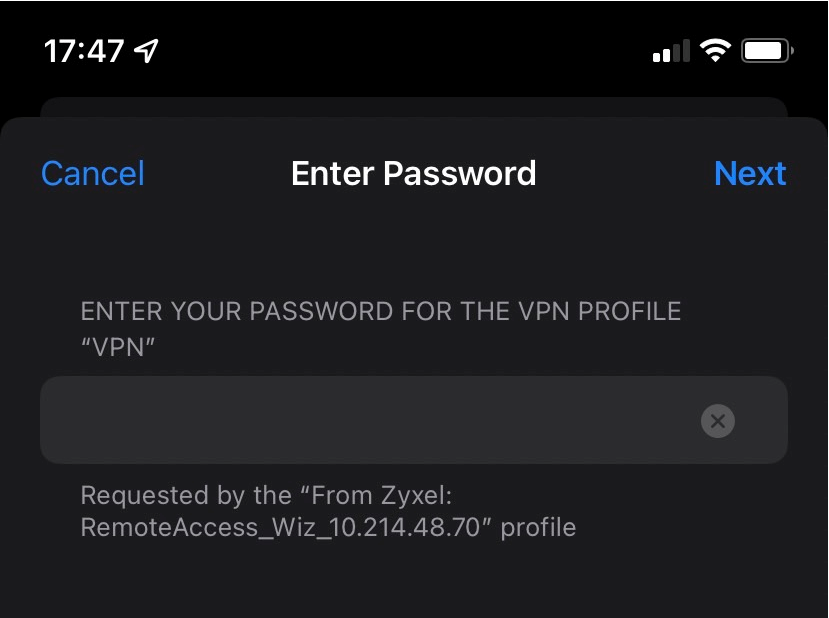
4. Enter Username and Password
5. Profile Installed Done
6. Now, it can connect
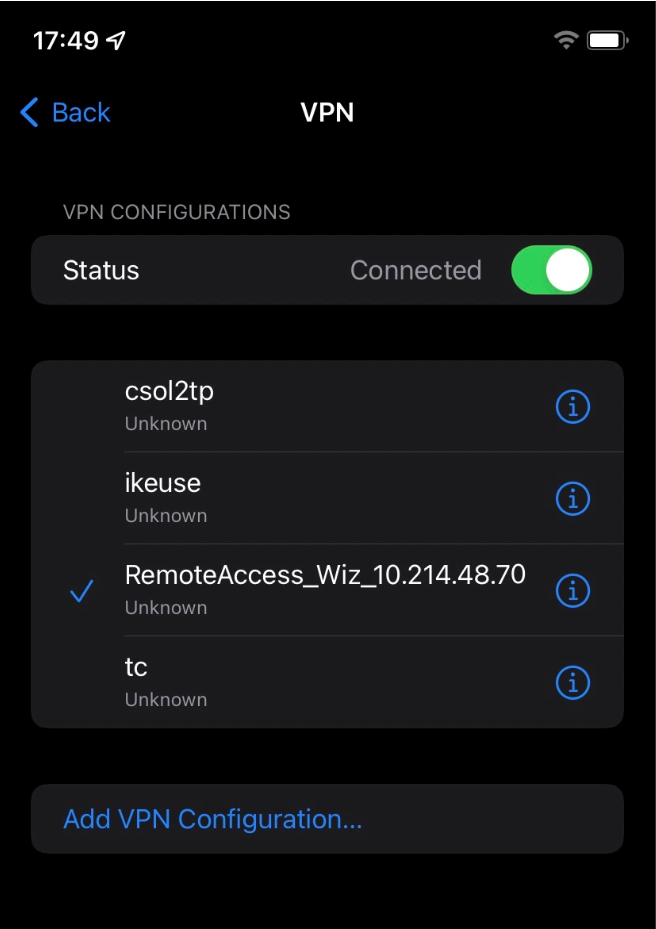
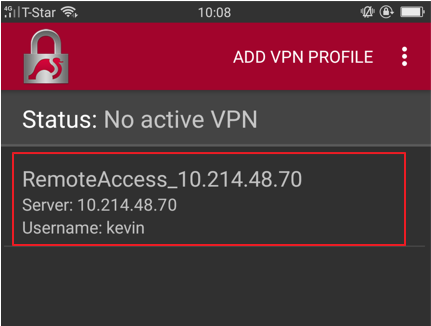
For Android: 1. Download strongSwan from Google Play Store

2. Send the Script to Device via email
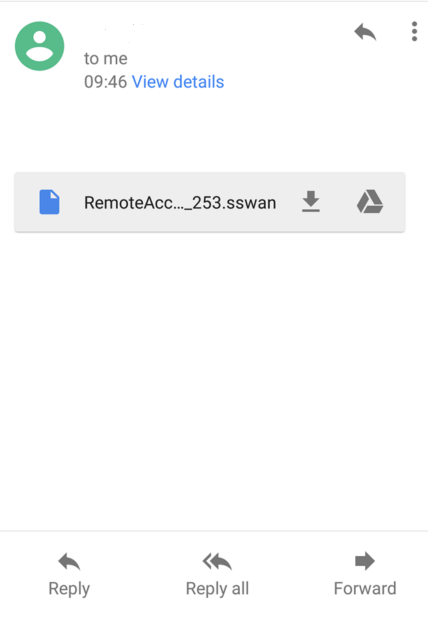
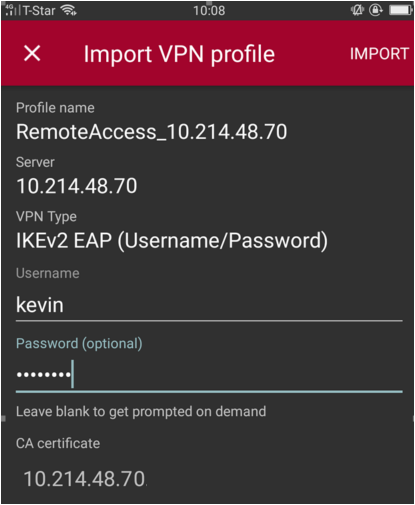
3. Import the Script into strongSwan and enter Username, Password
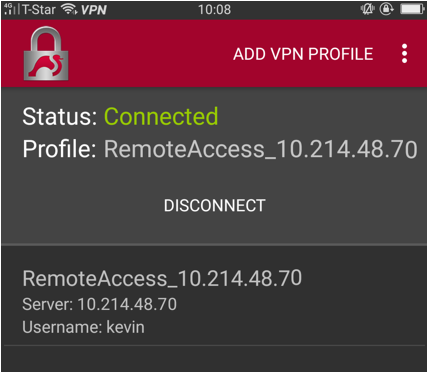
4. Now, it can connect.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 603 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight