[2026 January Spotlight] Integrate Secure Cloud Authentication with the USG FLEX H series
 Zyxel Employee
Zyxel Employee



As organizations adopt cloud services and support remote and hybrid work models, identity has become a critical foundation of modern security. Traditional authentication methods based on locally managed accounts are increasingly difficult to scale and protect against today’s threats, including credential theft and unauthorized access.
To meet these challenges, businesses are shifting toward centralized, cloud-based authentication models that enhance security while simplifying user access. This approach helps organizations reduce administrative overhead, support multi-factor authentication, and deliver a more consistent and secure login experience across users and locations.
This evolution reflects a broader move toward identity-driven security at the network edge.
🛡️Secure Cloud Identity on the USG FLEX H Series
The USG FLEX H Series brings modern cloud-based authentication to Captive Portal and SSL VPN, delivering enterprise-grade identity security for network access. With built-in support for OpenID Connect (OIDC), organizations can authenticate users through trusted identity providers such as Microsoft Entra ID and Google, without relying on locally managed firewall accounts.
This capability simplifies identity management, strengthens security through centralized authentication and multi-factor authentication, and delivers a smoother login experience across both remote access and network onboarding scenarios.
Available in uOS 1.37
To start using secure cloud authentication for Captive Portal and SSL VPN, make sure your USG FLEX H Series is updated to uOS 1.37 or later.
💡How Secure Cloud Authentication Works
The USG FLEX H Series extends secure cloud authentication directly to the network edge, enabling users to authenticate through trusted cloud identity providers without creating or managing local firewall accounts. When users access network services such as SSL VPN or Captive Portal, authentication is delegated to existing cloud identity platforms, allowing the firewall to verify identity without handling user credentials.
This approach centralizes identity verification, keeps credentials outside the gateway, and enables consistent access control across both remote and on-site access scenarios.
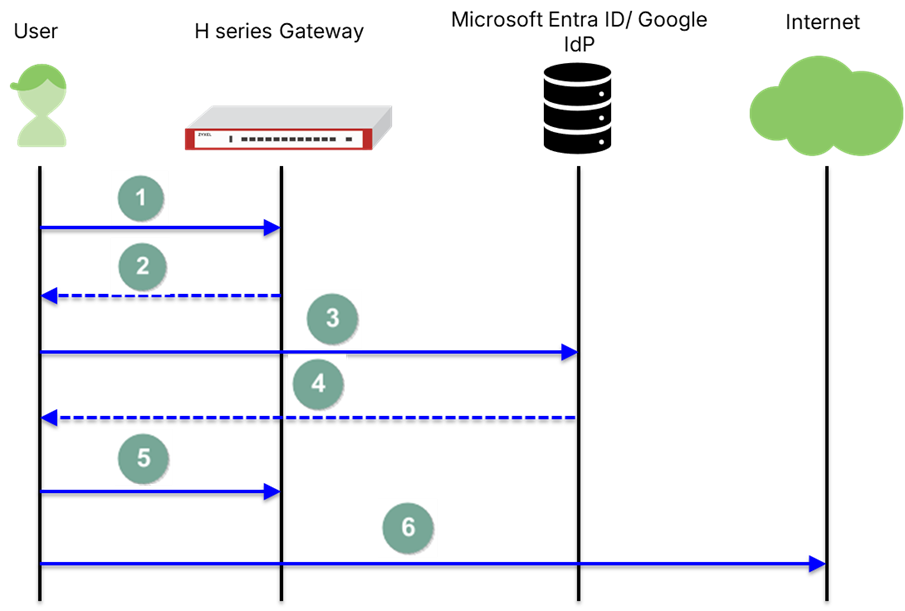
🔑Seamless and Secure Authentication Flow
- User access request: A user tries to access a service (SSL VPN, Captive Portal) through a configured OIDC-enabled gateway.
- Redirect to Identity Provider: The H series Gateway redirects the user to a trusted IdP (Microsoft Entra ID or Google)
- User authentication: The user completes the login process on the IdP's page.
- Obtain authentication token: Upon successful authentication, the IdP issues an authentication token to the user.
- Gateway token validation: The user returns to the gateway with the authentication token, and the gateway validates the token's validity and determines the user's access permissions.
- Grant access: Once validation is successful, the gateway allows the user to access.
This approach keeps credentials out of the firewall, reduces attack surfaces, and aligns with modern Zero Trust principles.
⚙️Configure Secure Cloud Authentication
The USG FLEX H Series supports secure cloud authentication across key access scenarios:
Using Microsoft Entra ID
Using Google
Step-by-step configuration guides with real-world examples and screenshots are available to help organizations get started quickly.
🛡️A Future-Ready Access Experience
By integrating secure cloud authentication directly into Captive Portal and SSL VPN, the USG FLEX H Series delivers a more secure, scalable, and future-ready access experience for modern workplaces and hybrid environments.
💭Already using the USG FLEX H Series?
We invite you to explore this new authentication capability and share your experience with us. What features or improvements would you like to see next? Your feedback plays a key role in shaping what comes next.
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 603 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 481 News and Release
- 92 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight