USG FLEX H Series - V1.36 Patch 0 Firmware Release
 Zyxel Employee
Zyxel Employee



Zywall USG FLEX H Series Release Note
October 2025
Firmware Version on all models
- Please use the cloud firmware upgrade function to upgrade USG FLEX H Series
| USG FLEX H Series | Firmware Version |
| FLEX50H | V1.36(ACLO.0)C0 |
| FLEX50HP | V1.36(ACLP.0)C0 |
| FLEX100H | V1.36(ABXF.0)C0 |
| FLEX100HP | V1.36(ACII.0)C0 |
| FLEX200H | V1.36(ABWV.0)C0 |
| FLEX200HP | V1.36(ABXE.0)C0 |
| FLEX500H | V1.36(ABZH.0)C0 |
| FLEX700H | V1.36(ABZI.0)C0 |
New Feature and Enhancements
1. [Enhancement] Nebula now supports Remote Access VPN (IPsec and SSL).
2. [Enhancement] Remote Access VPN (IPsec and SSL) now supports Nebula Cloud Authentication.
3. [Enhancement] Added a new default deny firewall policy “WAN_to_Device” with logging disabled.
4. [Enhancement] Support secondary peer gateway for VPN failover and fallback.
5. [Enhancement] IPsec VPN Phase 2 Policy now supports user defined name, allowing users to define the name when creating a Phase 2 policy. The name cannot be edited afterward.
6. [Enhancement] SSL VPN now supports setting the Minimum TLS Version to TLS1.3.
7. [Enhancement] Support for using a policy-based VPN tunnel as the next hop in Policy Routes. Special Notice: VPN tunnel with dynamic peer is not supported as the next hop in Policy Routes and are planned for a future release.
8. [Enhancement] Support the “Click-to-Continue” sign-in method for Captive Portal *Local only.
9. [Enhancement] Captive Portal (*Local only) enhancements:
a. Authentication Policy Criteria: Now includes Source IP and Destination IP fields.
b. External Portal: User can now configure an external portal.
c. Idle Timeout: Added configurable idle timeout in Advanced Settings.
d. Captive Portal support after login redirect.
10. [Enhancement] Support IGMP Proxy *Local only. [eITS#240301648]
11. [Enhancement] BWM categories support Tik Tok application service object [eITS#230200174]
12. [Enhancement] GUI enhancements:
a. Added validation to ensure User-Defined Trunks are not empty.
b. Geo IP address objects now support keyword search. [eITS#250401186]
c. Added a tooltip to display the country name when hovering over the flag in log entries. [eITS#250200264]
d. i-note added to clarify that the “Get from Server” function in SecuExtender only supports user-type accounts. [eITS#250601486]
e. Group objects display a warning if members exceed the maximum. [eITS#250700111]
13. [Enhancement] System Dashboard Storage usage add system storage usage information. [eITS#250701992]
14. [Enhancement] Diagnostic enhancements:
a. Add CLI option for SIP Pinhole logs and can download diagnostic file
b. Add CLI option for Device HA diagnostic logs to local storage and can download diagnostic file.
15. [Feature Change] Change DoS Prevention block destination to block source for flooding attack.
16. [Feature Change] Remote Access VPN: Download configuration files for multiple OS in one file.
17. [Feature Change] Change the default WAN trunk algorithm to LLF and the default algorithm is now configurable.
18. [Feature Change] New NAT rule defaults—Mapping Type = Virtual Server, External IP = Any, NAT loopback disabled.
19. [Feature Change] Removed the “Active Protocol” and “Encapsulation” columns from the Route-based VPN Phase 2 policy table.
20. [Feature Change] Renamed “SIP ALG” to “SIP Pinhole” since SIP Transformation is not supported. [eITS#250800156]
21. [Feature Change] Enlarge USG FLEX 700H maximum Address Object from 1000 to 1500.
22. [Feature Change] Enlarge USG FLEX 700H maximum Static Route rules from 512 to 1000.
23. [Feature Change] Updated packet flow order to process Dynamic/Site-to-Site VPN after Policy Route and Direct Route, ensuring VPN traffic follows configured routing rules.
AP controller New Feature and Enhancements
1. [Enhancement] Support Per AP radio and power settings
2. [Enhancement] Support WiFi 7 MLO
3. [Enhancement] Support Allow/Block list in MAC filter setting
4. [Enhancement] Support Hidden SSID
5. [Enhancement] Smart-Mesh support MLO on UOS
6. [Enhancement] Support AP Load Balancing
7. [Enhancement] Support AP Roaming Group
8. [Enhancement] Support override AP tag
9. [Enhancement] DFS channel switch enhancement
Bug Fix
1. [eITS#250400353] SNMP memory leak caused firewall hang itself.
2. [eITS#250500843] Site-to-site VPN traffic is being directed to the wrong security policy from WAN to ZyWALL.
3. [eITS#250501078] The IKEv2 VPN connection cannot be established. The error log shows: “Generating IKE_AUTH response 2 [EAP/FAIL]” due to the join Domain password containing the character ", which causes the radius daemon to fail to load.
4. [eITS#250501450] Unable to search for IP addresses in the DHCP list.
5. [eITS#250600093] DDNS update always fails when configuring ipv64 as custom DDNS.
6. [eITS#250600635] Enabling the DNS filter causes the device to crash.
7. [eITS#250600733] The client did not appear in the NCC client list as expected.
8. [eITS#250601306] Unable to copy the security policy to the number that more than the number after applying search filter.
9. [eITS#250700999] IPSec traffic hit wrong zone.
10. [eITS#250701097] The 1:1 NAT outbound routing rule only works when it has the highest priority, because the firewall matches the wrong NAT rule index.
11. [eITS#250701233] Internet access is disconnected unexpectedly.
12. [eITS#250701335] Client usage is not reported when the interface name contains specific characters.
13. [eITS#250701580] Site-to-site VPN traffic is being directed to the wrong security policy from WAN to ZyWALL.
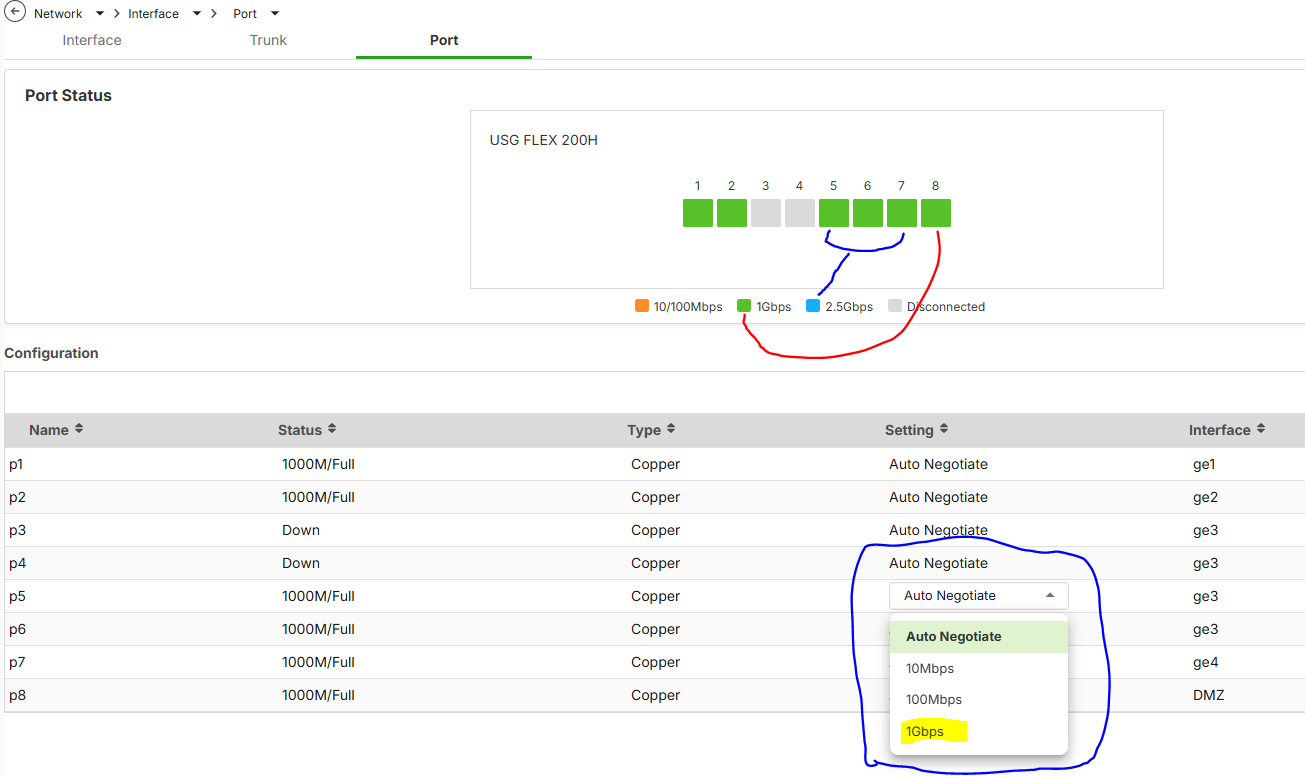
14. [eITS#250701830] When powering up the device, the port will be down and you need to replug the physical cable to bring the port up again. This is due to the device configuration file’s interface port speed missing the “auto” setting.
15. [eITS#250701902] pppoe interface link down doesn't update the default route trunk.
16. [eITS#250701904] The same MAC address can be configured for two IP address in lower and upper case in DHCP Reservation.
17. [eITS#250701969] The External Group User cannot retrieve the corresponding Group Identifier parameter.
18. [eITS#250701992] Client usage is not reported when the interface name contains certain characters.
19. [eITS#250800164] External group AD user auth failed when building up the VPN tunnel.
20. [eITS#250800924] Policy route rule affects site to site VPN tunnel traffic.
21. [eITS#250801108] Routing rule becomes inactive after rebooting.
22. [eITS#250801114] Security Policy rule (destination zone is WAN) will affect traffic which belonging to VPN zone.
23. [eITS#250900241] The number of scanning files of Sandboxing remains the same even after several hours.
24. [eITS#250900322] show state to see the current trunk state.
25. [ZNGA-4518] [AAA] The joining status is "Not join AD Domain yet." after reboot.
26. [ZNGA-8190] SSL VPN works properly when using an AD server as the Secondary authentication server and allowing External Group Users, but ext-group-users are not shown on the Login User page.
Nebula Bug Fix
1. [eITS#250701597] When saving a public IP as a CAPWAP server via NCC, the Nebula reported an error.
2. [eITS#250701910] The interface displays incorrect information in the mobile app.
3. [eITS#250800121] H Firewall config cannot sync with Nebula since the config is converted by converter.
4. [eITS#250800229, 250800838, 250801367, 250801574] The configuration status shows "Not up to date" due to inconsistent data from Nebula.
5. [eITS#250800653] Configuration override failed on Nebula due to an invalid character in the description field.
6. [eITS#250800836, 250800837] Receive delayed email alerts when a device goes offline in Nebula.
7. [eITS#250800843] The firewall LAG interface zone changes from the LAN zone to "none" for no apparent reason.
8. [eITS#250801187] After you assign a USG FLEX 500H to a site on Nebula, the configuration on Nebula will be reset to default.
9. [eITS#250801226] Can't delete VPN connection settings.
10. [eITS#250801372] Register a new device via NCC, but NCC is unable to click "Next" in Add devices.
11. [eITS#250900076] PPPoE Interface syncing issue between Nebula and firewall.
AP Controller Bug Fix
1. [RM:63836] Modifying AP group names sometimes fails.
2. [RM:63867] Disabling Smart Mesh feature does not automatically disable wireless bridge.
3. [RM:63873] Error occurs when configuring special characters with UTF-8 SSID names enabled.
Please refer to the Download Link for more details.
Comments
-
This is great:
15. [Feature Change] Change DoS Prevention block destination to block source for flooding attack.
Someone should probably update the manual, which still says:
Flood Detection applies blocking to the destination IP address and Scan Detection applies blocking to the source IP address.
https://webhelp.zyxel.com/search.action?model=USG%20FLEX%2050H&majVer=V1.36&minVer=&fwID=ACLO&lang=EN&hash=context/Help/SecurityPolicy_DoSPrevention_Policy&help_version=21 -
Thanks for pointing it out! We will arrange the resources to update it.
Zyxel Nebula Support
1 -
The online help wording has been updated.
Zyxel Melen0 -
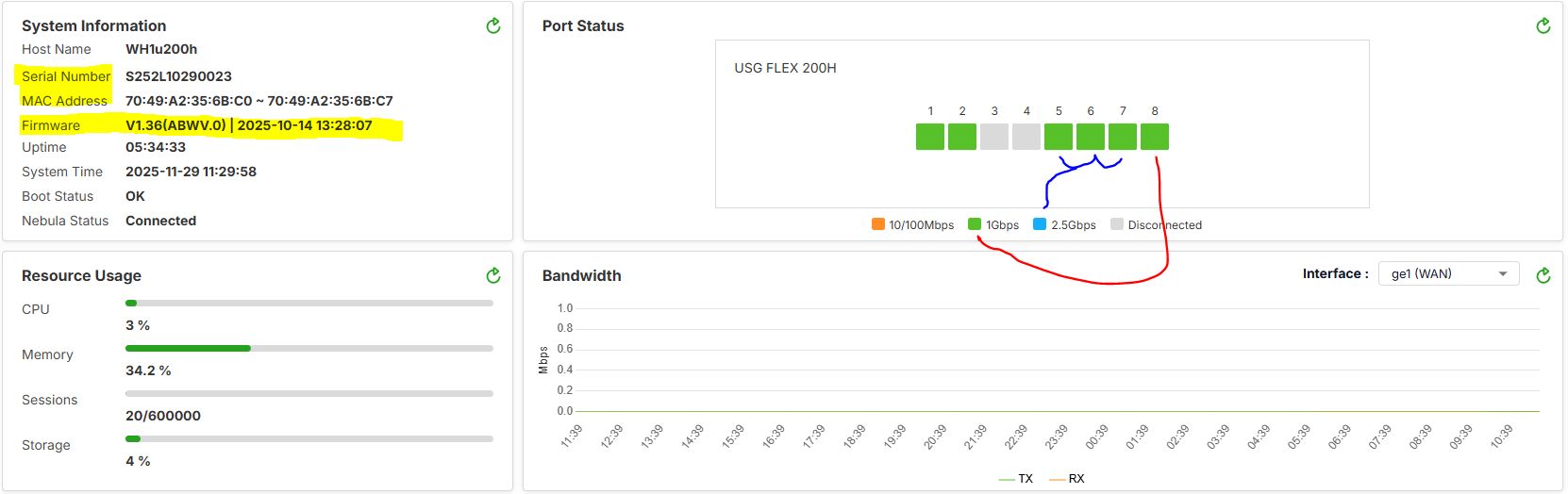
Have MAJOR issue with this patch - it removed the 2.5Gb capability from the LAN ports 3 through 8 (GE3 & GE4) on my FLEX 200H acquired under Zyxel Rewards Program - SKU: USGFLEX200H-USAM01F.
Tried reverting back earlier version, but nothing restores the speed
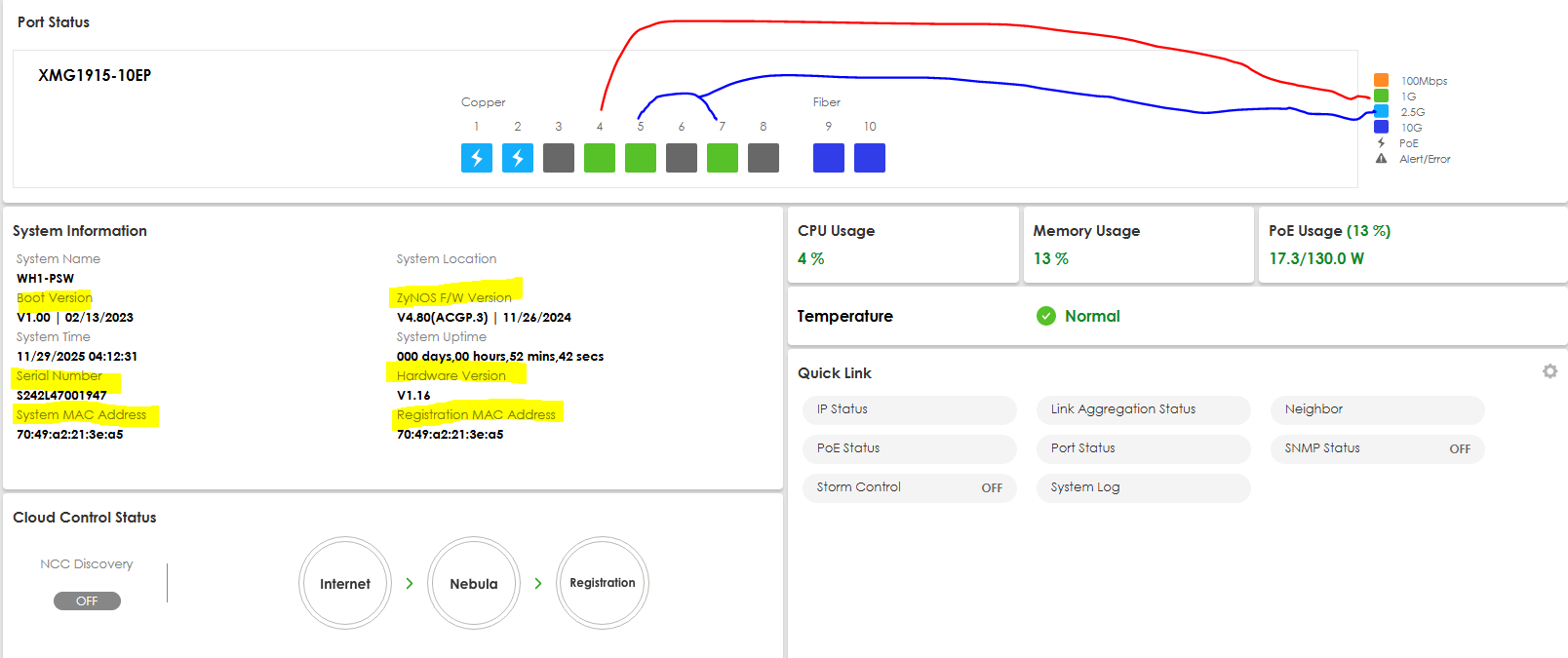
Shown are Ports 5 & 7 connected to the XMG1915EP which are 2.5Gb ports and indicated on the Flex 200h prior to the firmware upgrade.
All specs show the Flex 200H purchased from ZyXel store as having 2.5Gb ports. The only reason I upgrade on the special offer from my FLEX 500 1Gb.
P5 - Zyxel XMG1915 Port 5 isolated as LAN1
P7 - Zyxel XMG1915 Port 7 isolated as LAN2
P6 - Zyxel MG108 Port 2 unmanaged extension switch
Also have Zyxel XMG108 which originally showed 2.5Gb on the FLEX 200H
Data Sheet comp list shows these all have 2.5Gb ports same as on current Flex 200H Store link - acquired under Zyxel Rewards Program - SKU: USGFLEX200H-USAM01F
Did I get a dud or a clone knock-off ???
On the XMG1915, the same port is used between the two devices where each is designated for its own LAN1=port5, & LAN2=7 on both FLEX200H & XMG1915 respectively.
.
0 -
On the FLEX200H only port 1 and 2 are 2.5Gb
0 -
About your issue, we will help you in this post.
VLAN issue for XMG1915-10EP — Zyxel Community
Additionally, just like we mentioned in other posts, USG FLEX 200H only ports 1 & 2 supports 2.5G.
Zyxel Melen0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 588 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 477 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Freshman Member
Freshman Member





 Guru Member
Guru Member

