[USG Flex H] - Cannot use Policy Control between devices in the same Zone
All Replies
-
OK, if I launch the Wireshark tool and ask who is the 192.168.10.250 (the printer), the reply is tell 192.168.10.4 (the IP address of the PC) and then reply the printer with the MAC Address.
After that I have a who has 192.168.10.4? Tell 192.168.10.1 (the Firewall bridge interface) and the reply is the MAC Address of the PC.
0 -
when you have Enable Intra-BSS Traffic blocking you should not get a ARP reply in the subnet of the VLAN from other devices but the MAC reply of the gateway.
0 -
Hi @Maverick87
Because the traffic is between the same LAN/VLAN, so the traffic will not forward to the firewall in normal cases. Therefore, you will need to manage the traffic on your switch. If the client is wireless connected, you will need to enable Intra-BSS Traffic blocking for the SSID like Peter mentioned.
Additionally, the AP and switch forward traffic within the same LAN/VLAN, and the firewall routes traffic to other IP subnets/LANs/VLANs. The duties of layer 2 and layer 3 devices differ.
Zyxel Melen0 -
Hi @PeterUK and @Zyxel_Melen
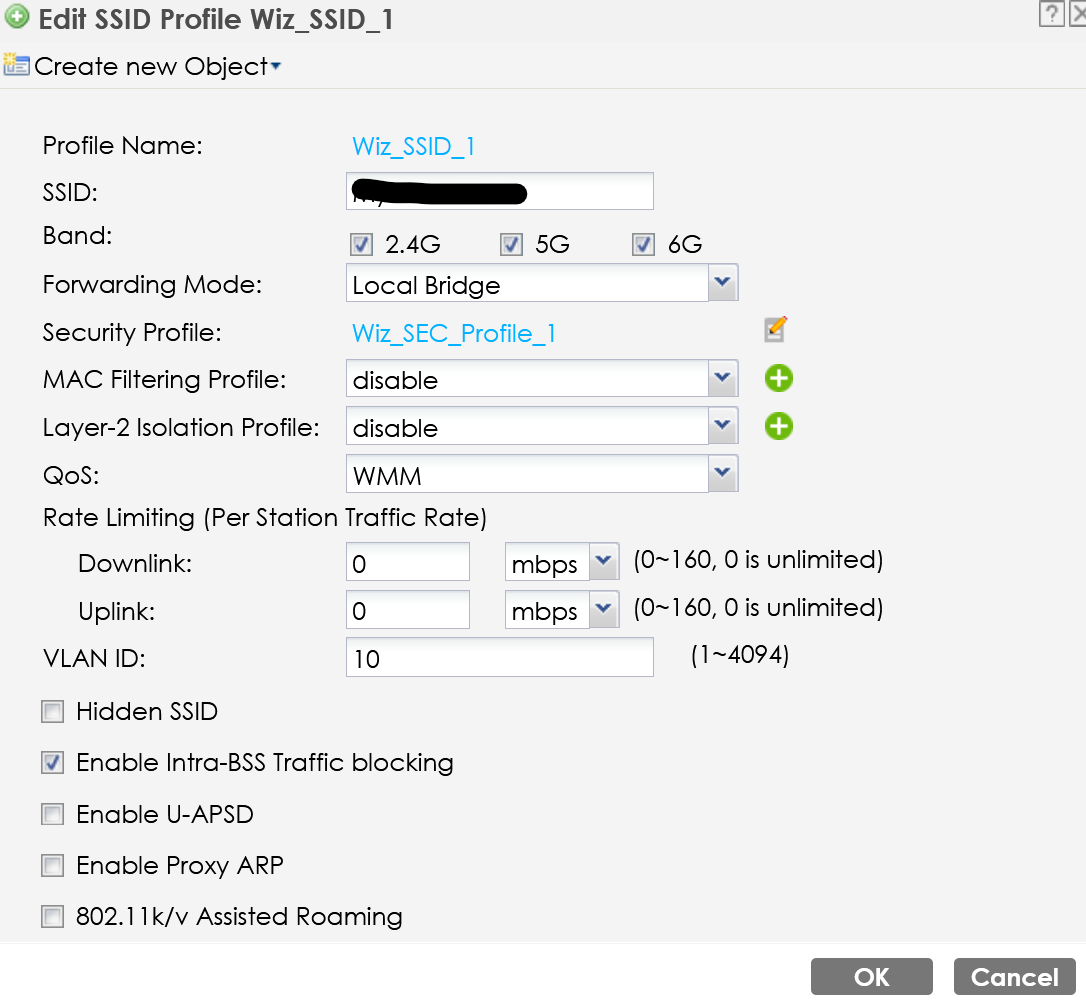
The AP configuration is this:
The only things that I've disabled is the Proxy ARP as suggested by PeterUK, but the Intra-BSS Traffic Blocking is already enabled.
But in this configuration, seems not working as expected.
Thank you
0 -
Melen could you check this option on FLEX H in SSH
vrf main interface ethernet test network-stack ipv4 arp-proxy enable
This does not seem to work?
On the ZLD you can enable this arp proxy with IP subnet and what happens is with enable Intra-BSS Traffic blocking client ARP for another client and a reply by USG for its MAC traffic is then send to USG then send out to the other client
0 -
Hi @PeterUK
I need to execute this on my FLEX H?
0 -
-
Yes but I tested it and it don't seem to work
I have a setup on my USG60W and it works clients to clients in the same subnet go through USG so you can firewall like from VLAN4093 to VLAN4093 with IP and port control.
0 -
yes sorry I meant true
vrf main interface ethernet test network-stack ipv4 arp-proxy true
I then commit and I do see in the config about arp-proxy for the given interface but does not seem to work?
0 -
Hi @Maverick87
So, is this the VLAN you mentioned in previous comment? Are the clients all connect to this SSID? If not, you still need to set ACL on the switch to block the traffic. The Intra-BSS Traffic Blocking only blocks the clients connecting to this SSID. If the clients is in AP's uplink, this feature will not block it.
Zyxel Melen0
Categories
- All Categories
- 442 Beta Program
- 2.9K Nebula
- 219 Nebula Ideas
- 127 Nebula Status and Incidents
- 6.5K Security
- 589 USG FLEX H Series
- 344 Security Ideas
- 1.7K Switch
- 84 Switch Ideas
- 1.4K Wireless
- 52 Wireless Ideas
- 7K Consumer Product
- 298 Service & License
- 478 News and Release
- 91 Security Advisories
- 31 Education Center
- 10 [Campaign] Zyxel Network Detective
- 4.8K FAQ
- 34 Documents
- 87 About Community
- 105 Security Highlight
 Ally Member
Ally Member

 Guru Member
Guru Member


 Zyxel Employee
Zyxel Employee